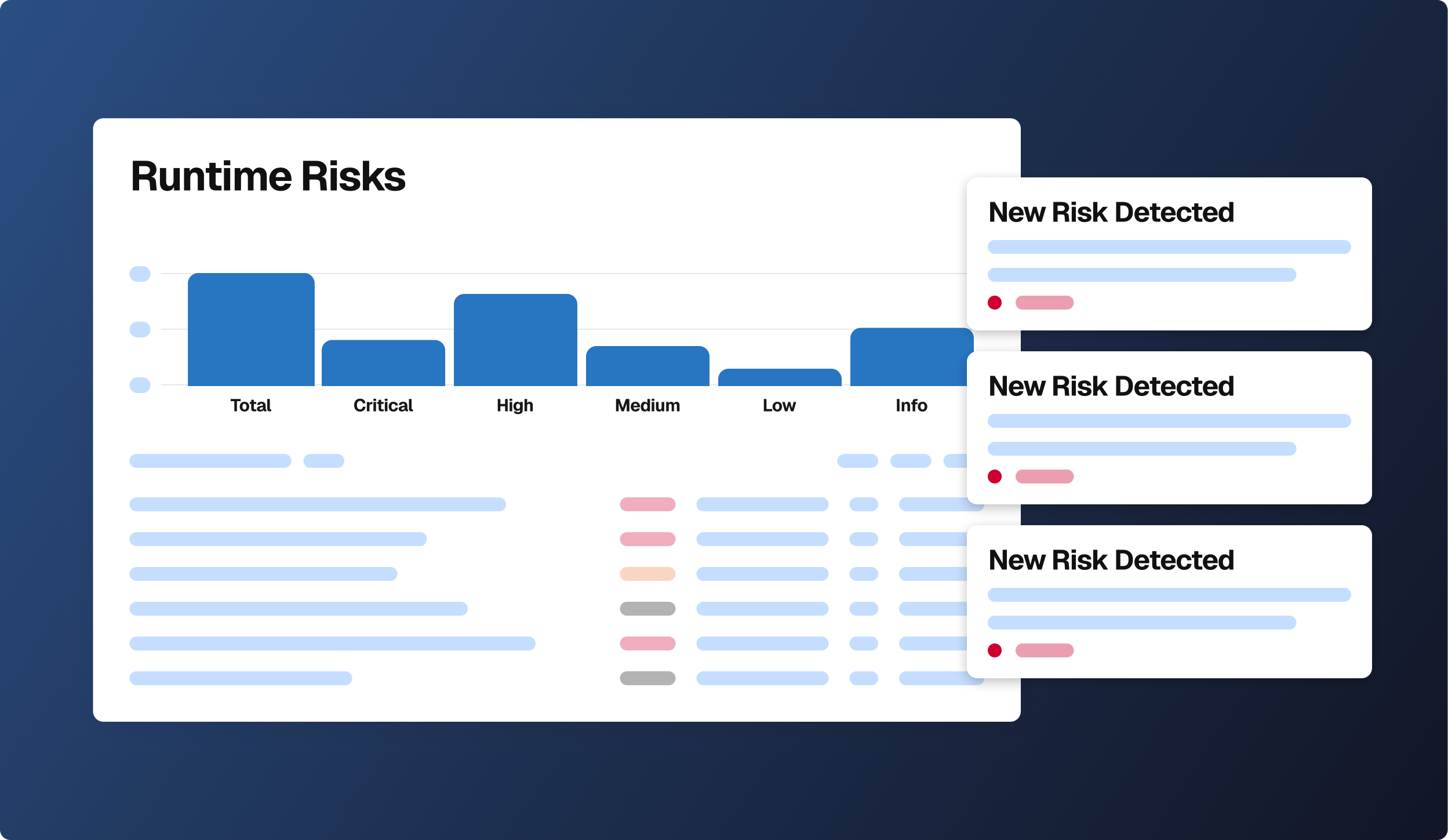
Real-Time Visibility Into Third-Party Software Risk
Third-party software is part of your attack surface, but your current tools can't see it. Spektion shows how third-party software behaves in your environment, beyond CVEs and vendor questionnaires.
Why Vulnerability Management and Third-Party Risk Management Miss Software Risk
Vulnerability Management (VM) and Third-Party Risk Management (TPRM) tools are useful, but they only cover part of the picture. Vulnerability Management tools stop at known CVEs. Third-Party Risk tools stop at questionnaires and certifications. Neither shows how third-party software behaves in your environment, where the real risk lives.
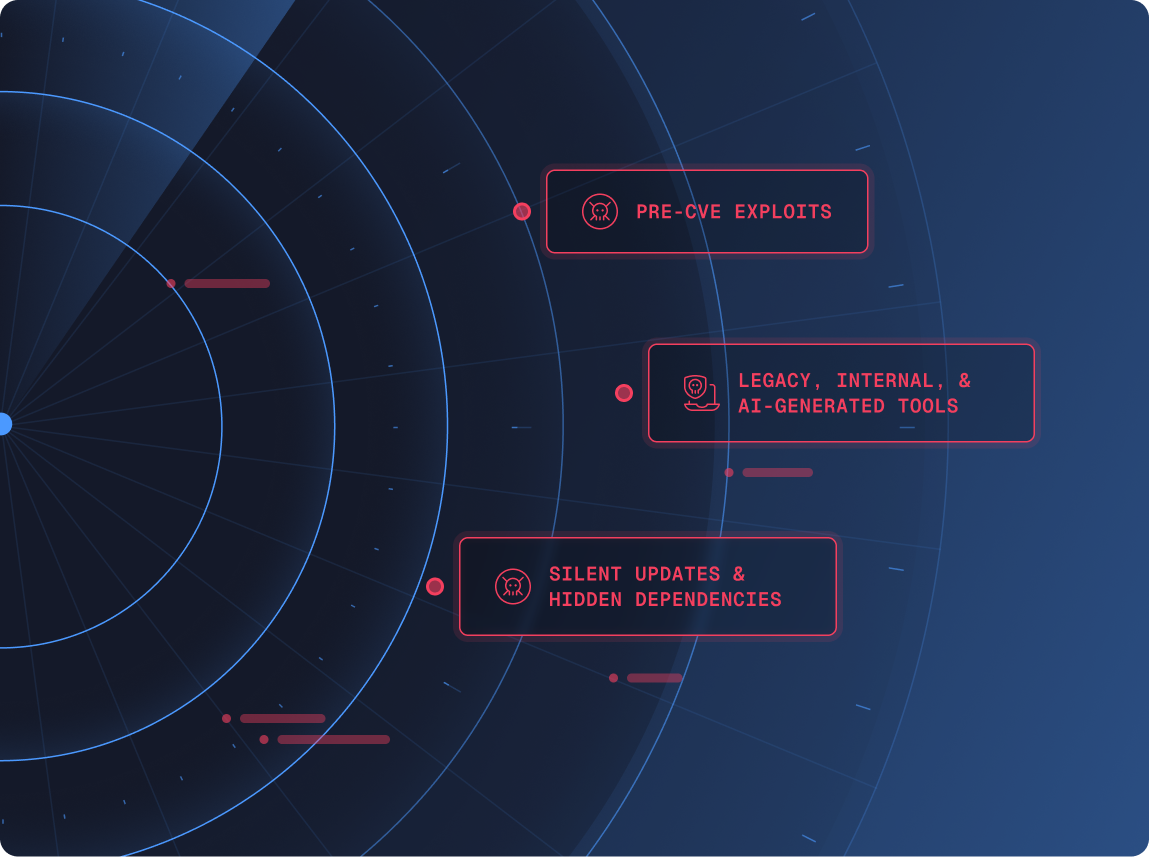
Both leave major gaps
- Pre-CVE exploits attackers use long before disclosure
- Legacy, internal, and AI-generated tools that will never receive CVEs
- Silent updates and hidden dependencies that slip past security review
Those gaps leave you exposed
of organizations with poor third-party visibility suffered a breach in the past year
of breaches in 2025 involved third-party software
of security leaders are concerned about third-party component risk
Runtime Visibility Into Third-Party Software Risk Closes the Gap
Spektion closes the gap with runtime visibility into third-party software behavior. We help you assess third-party software risk by showing what’s exploitable right now, with evidence from your environment, so your vulnerability management and third-party risk programs finally have the data they’ve been missing.
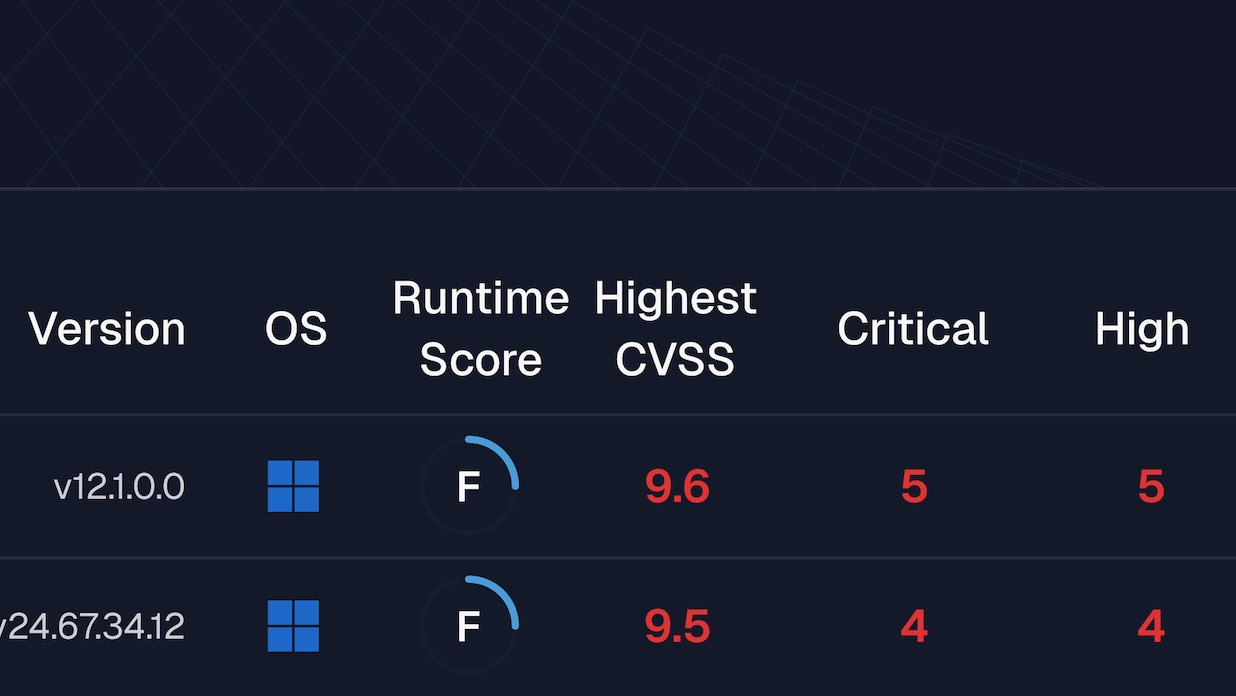
See Spektion detect risk in live software
How Runtime Visibility Reduces Risk
Build a live inventory, including shadow and unmanaged tools.
Spot privilege escalation, injection, hijacked updaters, and insecure network activity.
Prioritize with runtime data enriched by CVE, CWE, ATT&CK, and threat intel.
Contain unpatchable risk and reduce exposure in real time.
Use Cases Across the Software Lifecycle
Spektion provides value at every stage of software adoption and use:
-
 POC & Vendor Evaluation. Catch insecure behaviors before you sign a contract and negotiate from a position of runtime evidence.
POC & Vendor Evaluation. Catch insecure behaviors before you sign a contract and negotiate from a position of runtime evidence. -
 Continuous Monitoring. Detect risks introduced by silent updates, accelerated AI-driven releases, or supply chain compromises.
Continuous Monitoring. Detect risks introduced by silent updates, accelerated AI-driven releases, or supply chain compromises. -
 Vendor Breach Response. Identify your blast radius instantly and apply compensating controls in minutes.
Vendor Breach Response. Identify your blast radius instantly and apply compensating controls in minutes. -
 Decommissioning. Verify removal and close out lingering exposures with runtime proof.
Decommissioning. Verify removal and close out lingering exposures with runtime proof.
Compliance as a Byproduct
Audit requirements don’t go away, but Spektion makes compliance easier by turning runtime evidence into audit-ready data.
With Spektion, you get:
- A continuously updated software register
- Change-of-risk alerts that prove ongoing monitoring
- Runtime logs to support incident response and vendor offboarding
- Evidence you can hand directly to auditors for DORA, PCI DSS, GLBA, and more
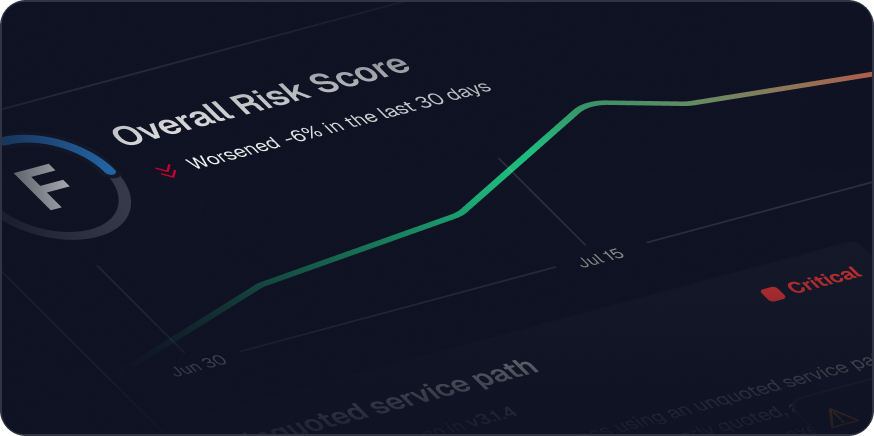
Compliance isn’t why leaders choose Spektion. It’s what happens naturally when runtime evidence powers your program.
Why Security Leaders Choose Spektion
Third-party software risk has lived between silos for too long, until now.
| Old way | With Spektion |
|---|---|
| VM leaders only see risk when a CVE exists | VM leaders get visibility into risky behaviors even without CVEs |
| TPRM leaders rely on questionnaires and certifications | TPRM leaders also validate third-party software with runtime evidence |
| CISOs manage silos and incomplete inventories | CISOs get a unified, real-time view of third-party software risk |
Spektion brings these perspectives together with a single source of runtime evidence.
The impact: Organizations using runtime visibility reduce exploitable exposures by double digits in weeks, cutting both operational risk and wasted patching effort.