Runtime Intelligence:
CTEM’s Missing Layer
CTEM is shaping the future of risk management, but without runtime intelligence, it can’t see the risks it’s meant to manage. Spektion reveals exploitable conditions as they occur and provides tailored mitigations so you can cut noise, shrink your attack surface, and reduce exposure continuously.
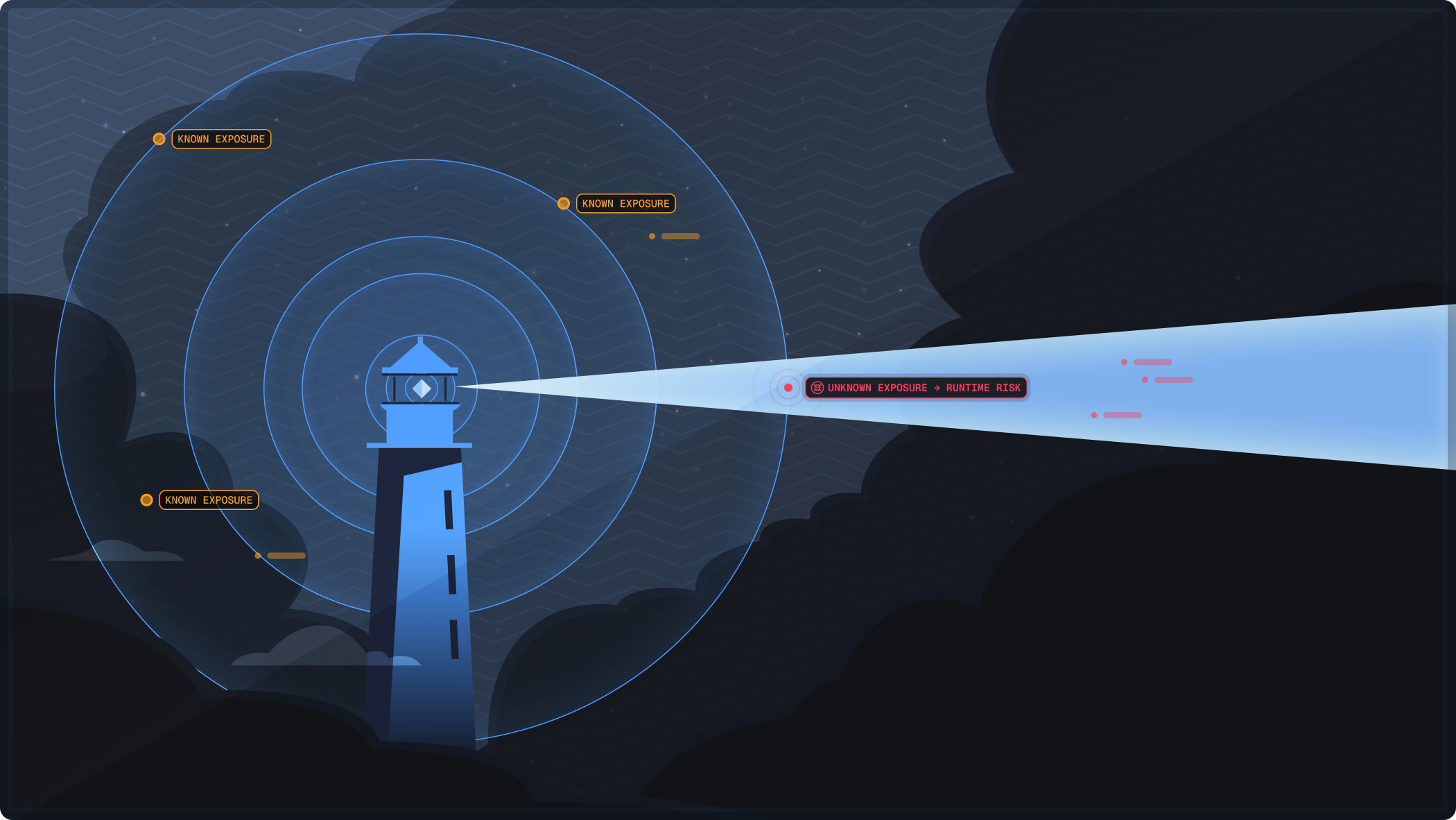
Software Exposure Is Growing Faster Than Teams Can Manage
Installed software, including authorized third-party apps, unauthorized installs, and internally-developed tools, often represents significant visibility gaps in modern CTEM programs. These gaps can include exploitable vulnerabilities without CVEs, risky network connections, and functionality that enables attackers to move across the network undetected. Without continuous runtime intelligence, these assets remain hidden behind static registries, leaving exploitable risks unaddressed.
Those Gaps Leave CTEM Programs Exposed
increase in breaches caused by software vulnerabilities year over year
of organizations need multiple days to build a complete software inventory
gap between the number of apps execs think are in use in their orgs vs what’s actually in use
Extend CTEM Programs to See What’s Actually Running
Spektion delivers runtime visibility intelligence, empowering CTEM programs to see what software is running, where it’s running, and how it behaves, turning unseen software into measurable risk reduction.
→ One Spektion customer uncovered 215 remote access tools through runtime monitoring, revealing previously unseen exposure.
→ Another reduced their software exposure footprint by 27% in just 30 days by identifying and removing unused software they were previously unaware of.
By combining continuous exposure monitoring with runtime behavioral analytics, customers can identify real exposures and reduce risk in real time, without relying solely on vendor disclosures.
See Spektion close the visibiity gap in CTEM programs
Runtime Evidence for Every CTEM Stage
Spektion brings the runtime intelligence that CTEM programs need to deliver results at every stage.




Continuous Runtime Visibility, Delivered in Minutes
Spektion translates complex runtime behavior into clear, actionable intelligence that supports every phase of your CTEM program, with fast deployment and minimal overhead.
With Spektion, security, IT, and CTEM teams gain:
- A live software inventory of everything that’s actually running across the estate, including versions, publishers, and usage.
- Runtime behavioral intelligence that automatically prioritizes exposure risk in real time and highlights which vulnerabilities don’t represent risk.
- Shared insight across security and IT, creating a single, trusted view of vulnerability risk for CTEM decisions.
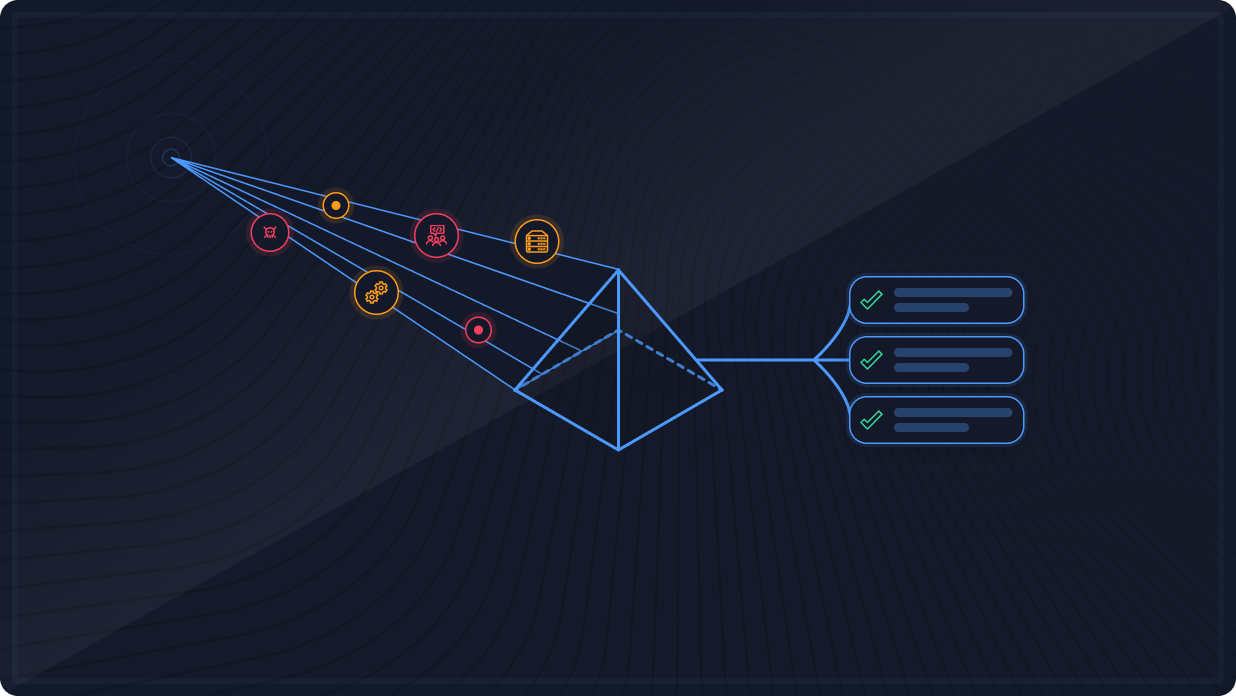
Spektion delivers continuous runtime insight that’s easy to implement and provides immediate value, helping CTEM programs focus on what’s exploitable and actionable in real time.
Why Security and IT Teams Rely on Spektion to Enhance CTEM Programs
CTEM programs depend on Spektion to uncover and prioritize exposures traditional tools miss, shifting remediation from reactive patching to continuous, evidence-based risk reduction.
| CTEM Challenge | Solved with Spektion |
|---|---|
| Incomplete software asset registry | Live map of active software, including unknown and unmanaged assets |
| Lagging or unclear view of risk in assets without CVEs | Live runtime-based risk scoring with exploitability and blast radius context, enriched with CVSS where applicable |
| Misalignment between security and IT teams | Shared visibility and progress tracking for CTEM workflows |
| No clear options for exposure reduction beyond patching | Prioritized remediation guidance, including preventive and detective compensating controls such as safe removal, reconfiguration, or targeted |
Spektion gives CTEM its missing runtime layer for real software exposure reduction.
The impact: Organizations using Spektion’s runtime intelligence reduce exploitable exposures by double digits in weeks, cutting operational risk and wasted patching effort.