Runtime Assurance for AI-Coded Apps
Spektion detects runtime risks from known and unknown internal tools, AI-enabled and low-code citizen development, and third-party software in your environment in real-time.
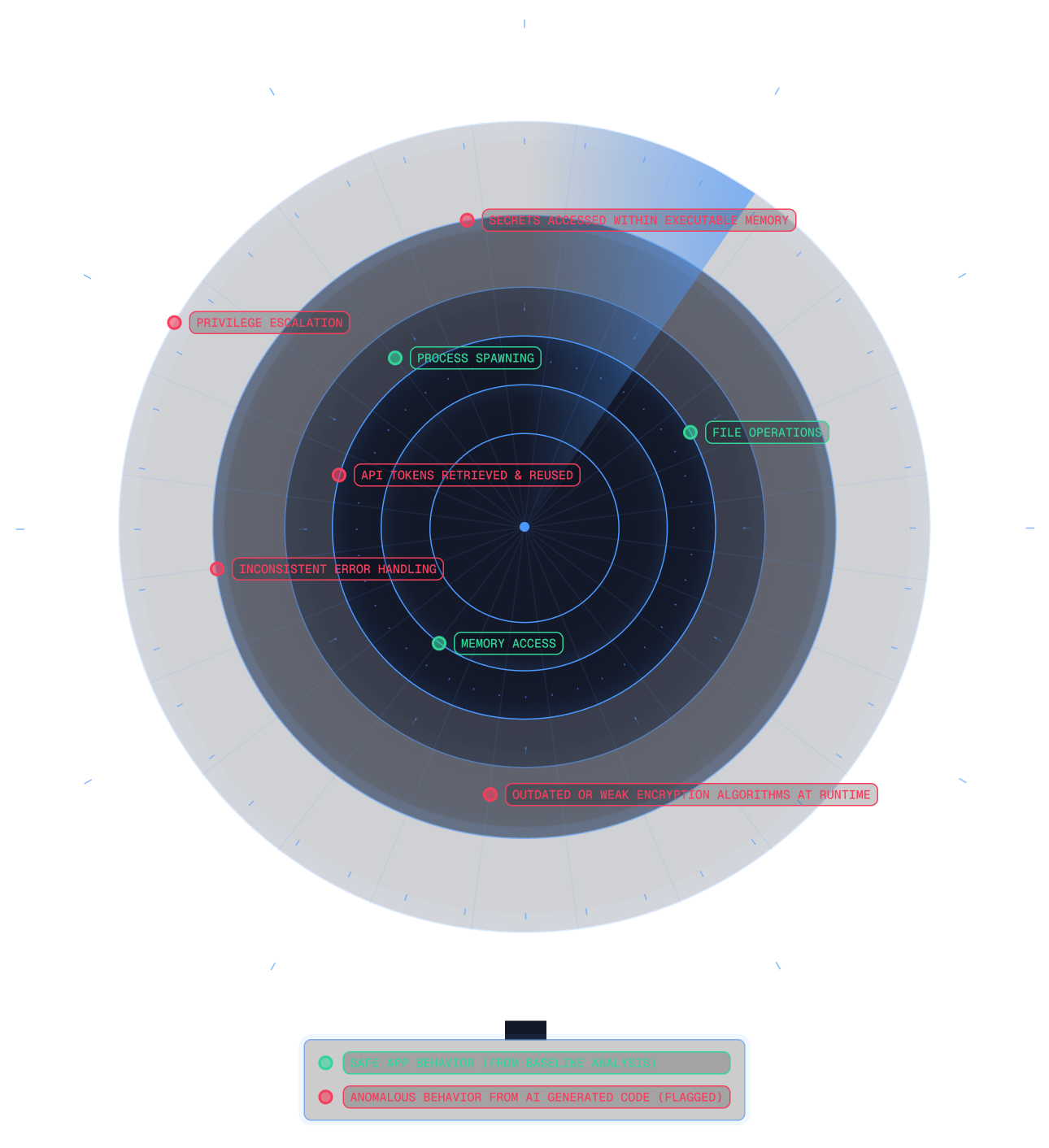
See Spektion Surface Exploit Risks in LLM-Coded Apps
Spektion is how vulnerability management teams can respond at speed and scale to software exploitation risk without stopping employees from building with AI. Our tool passively monitors all your software at runtime, showing a live view of risk regardless of how an application was built.
AI-Enabled Development Is Growing Your Attack Surface
AI and low-code tools make it easy for anyone in your organization to quickly build and deploy applications without security safeguards, increasing exploitation risks through:
-
 Hallucinated Dependencies. 20% of repeatedly recommended packages called by AI don’t exist, creating a predictable attack surface. (University of Texas at San Antonio, 2025).
Hallucinated Dependencies. 20% of repeatedly recommended packages called by AI don’t exist, creating a predictable attack surface. (University of Texas at San Antonio, 2025). -
 Hardcoded Secrets & Client-Side Authorization. LLMs often include API keys, tokens, or credentials directly in code or rely on insecure client-side authentication, making it easy for attackers to harvest keys or tokens.
Hardcoded Secrets & Client-Side Authorization. LLMs often include API keys, tokens, or credentials directly in code or rely on insecure client-side authentication, making it easy for attackers to harvest keys or tokens. -
 No Secure Defaults. AI code assistants create “significantly less secure code” (Stanford University 2023). LLMs frequently skip security basics, such as input validation, secure cookies, or logging.
No Secure Defaults. AI code assistants create “significantly less secure code” (Stanford University 2023). LLMs frequently skip security basics, such as input validation, secure cookies, or logging. -
 Shadow IT Expansion via Non-Devs and “Vibe Coding”. Non-technical staff are using AI to spin up apps, often with no security reviews. Internal tools handling sensitive data can go live without anyone being aware of their existence.
Shadow IT Expansion via Non-Devs and “Vibe Coding”. Non-technical staff are using AI to spin up apps, often with no security reviews. Internal tools handling sensitive data can go live without anyone being aware of their existence. -
 Developer Overtrust In AI-Generated Code. 48% of AI-generated code snippets contain vulnerabilities (Georgetown University 2024). Yet, the majority of developers, professional and amateur, assume AI-generated code is “secure by default” or lack the capacity to review code at speed.
Developer Overtrust In AI-Generated Code. 48% of AI-generated code snippets contain vulnerabilities (Georgetown University 2024). Yet, the majority of developers, professional and amateur, assume AI-generated code is “secure by default” or lack the capacity to review code at speed.
Spektion Gives You Runtime Visibility Into AI-Written and Low-Code Apps In Your Environment
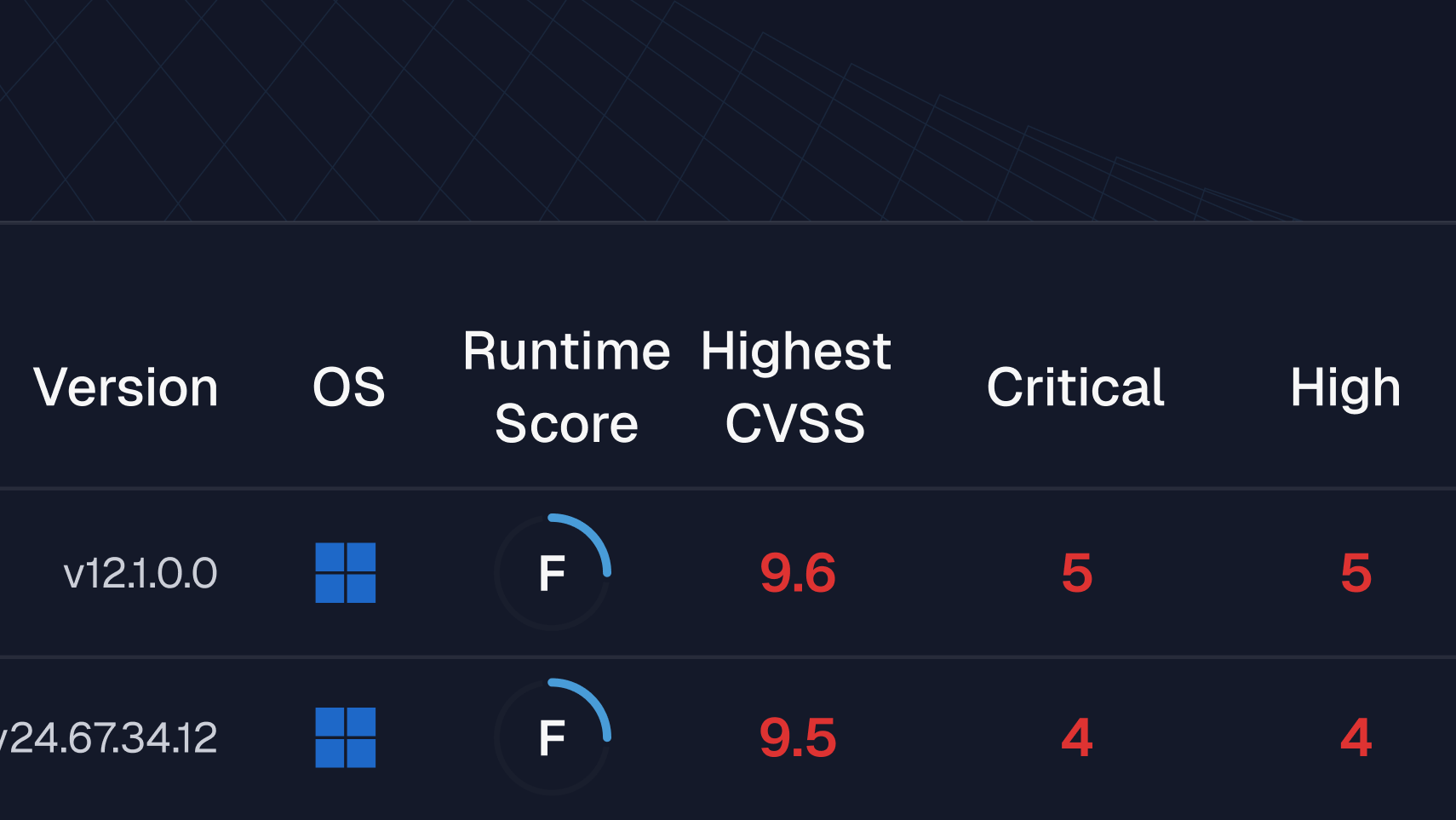
Spektion’s Runtime Vulnerability Management (RVM) technology can detect and prioritize exploitable vulnerabilities in the AI-coded apps that already live in your environment, even in applications you don’t manage.
Here's how:
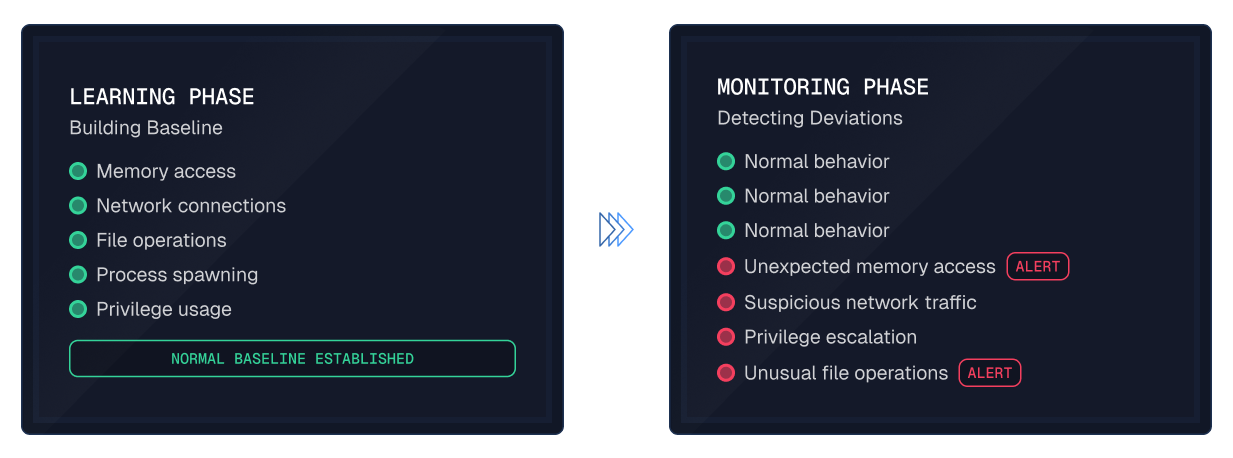

Automated App Discovery and Vulnerability Management
Spektion observes software applications, including low-code apps and LLM-coded tools, whenever they connect to your internal systems. This encompasses unauthorized apps that are not on your software registry.
LLMs may reuse insecure patterns or invent unsafe logic. Spektion identifies runtime risks like:
- Excessive privilege flaws that aren't tied to known CVEs.
- Data security risks, such as utilization of insecure crypto.
- Execution risks, such as insecure memory management, can still exist even if the code passes SAST/DAST.
Spektion acts as a runtime “tripwire” layer, flagging anomalies in all software (regardless of who coded it), so IT teams can get certainty into what’s actually active and dangerous.
Spektion doesn't care how an application’s code was written; it detects real risks created by an app at runtime. This results in far fewer false positives and extremely accurate prioritization.

Detect AI-Coded Vulnerabilities That Scanners Miss
Spektion helps you transform vulnerability management from a reactive, signature-based process into a toolkit for managing high-tempo software risks, shadow IT, and vulnerabilities without needing access to source code.
| Risk Type | Vulnerability Scanners | Spektion Runtime Monitoring |
|---|---|---|
| Unknown internal tools and citizen dev apps | ❌ Not in asset inventory | ✅ Detects when they connect to internal systems |
| Risks from AI-enabled rapid development | ⚠️ May be visible in some deployment tools | ✅ Flags risky runtime execution behavior |
| Third-party software with unknown updates | ⚠️ Version tracking only | ✅ Detects behavioral changes in real-time |
| Shadow IT deployments | ❌ Completely invisible | ✅ Catches runtime execution behavior |
| Privilege escalation in unknown apps | ❌ | ✅ Flags runtime privilege requests |
Try a Vulnerability Management Solution Made for the AI Age
Manage AI-Driven Risk Without Adding Headcount or Blocking Innovation
Spektion detects risky behavior from all software running in your environment, not just the apps IT are aware of. This includes AI-generated code, low-code tools, internal scripts, open-source components, and unsanctioned shadow IT.
Whether software was written by a senior developer in your organization, generated in a Copilot prompt, or supplied by a third-party provider, Spektion sees signs of real exploitation before CVEs even exist, including:
- LLM-coded apps retrieving secrets with over-permissioned access.
- Business apps unexpectedly accessing sensitive memory regions.
- Citizen-built dashboards initiating insecure outbound connections.
- AI-generated services requesting elevated privileges.
- Runtime behaviors that resemble known malware patterns.
By combining behavioral signals with environmental context, Spektion gives you focused risk intelligence, so you can act on what’s actually dangerous, not just what scanners flag as “vulnerable.”
AI-Generated Code Security Risk Reduction FAQs
Spektion monitors any software that runs in your environment, including:
- AI-generated code (LLM/Copilot).
- Internal tools and scripts.
- Low-code/no-code apps.
- Open-source components.
- Third-party software.
- Shadow IT or citizen-developed apps.
Yes. Spektion can find apps built with AI in your environment, including apps created with ChatGPT or Copilot.
Spektion doesn’t rely on asset inventory or known codebases. It observes runtime behavior, meaning that it can detect risky activity even from unregistered or unsanctioned apps.
No. Spektion examines what code does when it runs, including API calls, privilege requests, memory access patterns, and unusual network behavior.
Spektion is a solution to evaluate all your software, including homegrown tools, and flag risks at runtime, as it is impractical to expect every internally-built one-off app to be subject to SAST and other secure SDLC tooling.
Yes. LLM-generated code often includes insecure defaults, over-permissioned logic, or insecure behavior when code calls hallucinated dependencies. Spektion identifies those risks when the code executes, even if there’s no CVE.
Scanners look for known vulnerabilities in known assets based on matching software with CVEs.
Spektion identifies unknown risks in real-time execution, covering:
- Non-CVE behavior.
- Unreviewed AI-generated code.
- Shadow IT activity.
- Exploitable misconfigurations in production.
No.
Spektion passively monitors your software behavior with no instrumentation, rewrite, or SDLC overhaul required.
Spektion’s RVM solution treats internally developed software the same as commercial tools.
It’s not AppSec for all of your homegrown apps; it’s a solution to manage the absence of AppSec, which is impractical when any employee can build their own software.
No. Spektion is an IT visibility and risk management solution. It's designed for environments where traditional application security processes don't apply, such as citizen developer tools, shadow IT, and frequently updated third-party software that exists outside your development pipeline.