Unquoted Paths: The Decades-Old Flaw Still Enabling Hidden Code Execution
Unquoted paths (CWE-428) remain a hidden threat in today’s software. See how runtime visibility exposes what legacy vulnerability tools overlook.
Published on
Summary & BLUF
Threat actors have long exploited applications that invoke executables through unquoted file paths. Despite years of guidance from Microsoft specifically on this risk and how to mitigate it, developers still “vibe code” their way into insecurity.
Whether it’s the well-documented methods that hijack service image paths and executable paths or newer methods that implement this flaw in new AI-focused malware families and proof-of-concepts, organizations continue to overlook the applications in their environment that fall prey to it.
Unfortunately, many enterprises still wait for a CVE before they attempt to harden their environments, which leaves them vulnerable. Vendors, still today, continue to produce software that contains this dangerous development flaw, and our data shows a CVE isn’t always assigned, although the risk is real.
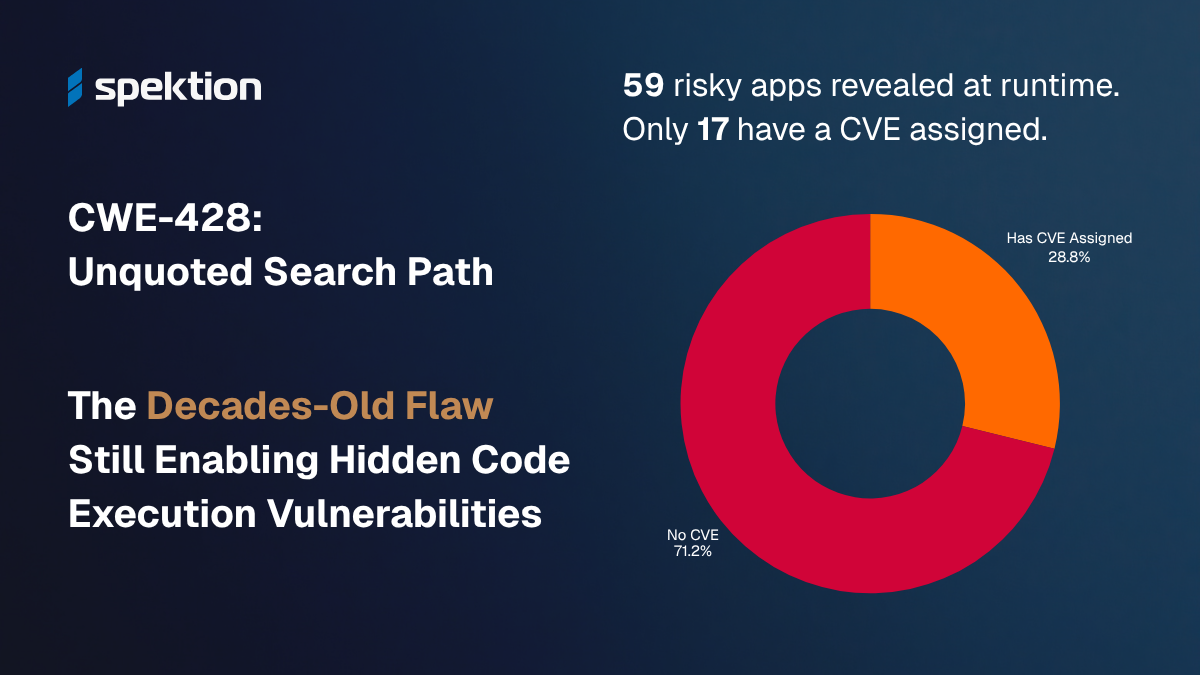
Only 30 vulnerabilities were published in 2025 that listed CWE-428 as their root cause.1 However, Spektion has observed this runtime risk in 19 separate categories of software, impacting 59 different applications, yet only 17 of the 59 (29%) have a CVE present at the time of this writing.
Impacted software without a CVE yet for this risk includes remote access solutions, file sharing tools, and other applications that actively accept network connections, which makes them prime targets for exploitation.
In this blog, we will elucidate the inherent insecurity of this runtime risk, highlight the fidelity of using it as a basis for other risk factors, and provide real-world examples of how it can be leveraged in attack scenarios.
Additionally, we will present metrics based on runtime data from our sensor telemetry and provide methods for threat hunting opportunities within your environment.
DET-00038: Spektion Detected Unquoted Path Execution at Runtime
Spektion detects when software calls CreateProcess or related APIs with unquoted executable paths at runtime and presents this risk to customers, allowing them to mitigate it.
The section below maps this runtime behavior to its MITRE ATT&CK and CWE counterparts, showing how a single developer oversight can become an attacker’s privilege-escalation technique.
T1574.0092 - Hijack Execution Flow: Path Interception by Unquoted Path
Adversaries can hijack vulnerable file path references by placing malicious executables in higher-level directories when paths lack quotation marks. Service and shortcut paths with spaces but without quotes are especially at risk for path interception due to how the CreateProcess function attempts to interpret filename possibilities in the absence of enclosed quotes.
CWE-4283 - Unquoted Search Path or Element
The product’s search path includes an unquoted element with spaces or separators, which may lead to accessing resources in a parent directory. If someone with malicious intent can modify the file system, they could escalate privileges by adding a file like C:\Malware.exe that a privileged program might run using WinExec or other available means.
CreateProcessA4 - A Behavioral Note
CreateProcessA, one of many CreateProcess variants that relies on path parsing without quotes (along with other APIs such as ShellExecuteEx), is the standard function to create a new process on a Windows system. Outlined below is a C++ Syntax overview of the function from Microsoft.
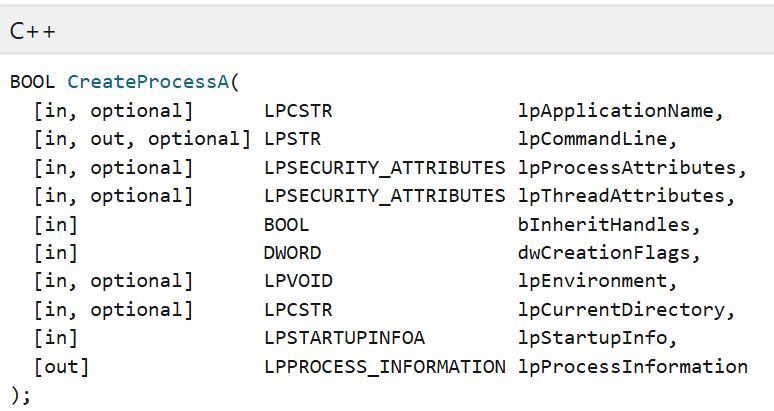
Figure 1: Source, Microsoft
Microsoft’s own documentation explicitly warns developers about this behavior:
“If you are using a long file name that contains a space, use quoted strings to indicate where the file name ends and the arguments begin; otherwise, the file name is ambiguous. For example, consider the string “c:\program files\sub dir\program name”. This string can be interpreted in a number of ways. The system tries to interpret the possibilities in the following order:
-
c:\program.exe
-
c:\program files\sub.exe
-
c:\program files\sub dir\program.exe
-
c:\program files\sub dir\program name.exe”
Real World Impact: New Vulnerabilities Arise From A 20+ Year-Old Flaw
30 vulnerabilities have been published in 2025 so far for CWE-428. Of those, 14 vulnerabilities have a CVSS score of 7.5 or higher.5
In a recent example, Dell published a high-severity (CVSS 7.8) vulnerability (CVE-2025-21107) impacting their Networker application.
“Dell NetWorker, version(s) prior to 19.11.0.3, all versions of 19.10 & prior versions contain(s) an Unquoted Search Path or Element vulnerability. A low privileged attacker with local access could potentially exploit this vulnerability, leading to Code execution.”
Dell Networker is a data protection application, which means an attacker with local access could not only take advantage of the vulnerability and attain code execution, but they could also potentially gain access to the resources the tool was designed to protect. Until this vulnerability was released, anyone running vulnerable versions and not taking advantage of runtime telemetry would have had no idea that they had unintentionally expanded their organizational attack surface.
Exploitation Scenarios
The most common exploitation scenarios for this runtime risk are:
Executable Hijacking
In this scenario, the attacker will place a malicious binary either in the same directory or the parent directory that corresponds to an existing image path for a service that already exists on the targeted system. When the service attempts to start, it will load the malicious file instead of the legitimate file due to how Windows attempts to determine the file location in the absence of quotes around the path string.
Privilege Escalation
Because each new process runs using the same permissions as the calling process, this is a very prominent method used for privilege escalation by malware and threat actors during post-exploitation or interactive intrusion phases.
Persistence via Path Hijacking
Like the executable hijacking scenario, except this method attempts to persist after a reboot and maintain persistence on a target computer by using paths that already have known associations (e.g., registry path, services). This is often chained with DLL hijacking, where a malicious DLL and executable will both take advantage of unquoted path strings.
Malware / Proof-of-Concept (PoC)6
Due to how reliant unquoted paths continue to be, newer PoCs have started to emerge that continue to use them, even when using a more advanced methodology. In the example of LOLMIL, the author is attempting to create “hypothetical self-contained C2-less malware” utilizing localized AI models that don’t rely on traditional C2 traffic, and the example code uses unquoted paths in the sample code. While the PoC remains theoretical, it exemplifies the continued developer negligence toward quoting executable paths.
Vulnerable Software Categories Identified by Spektion’s Runtime Data
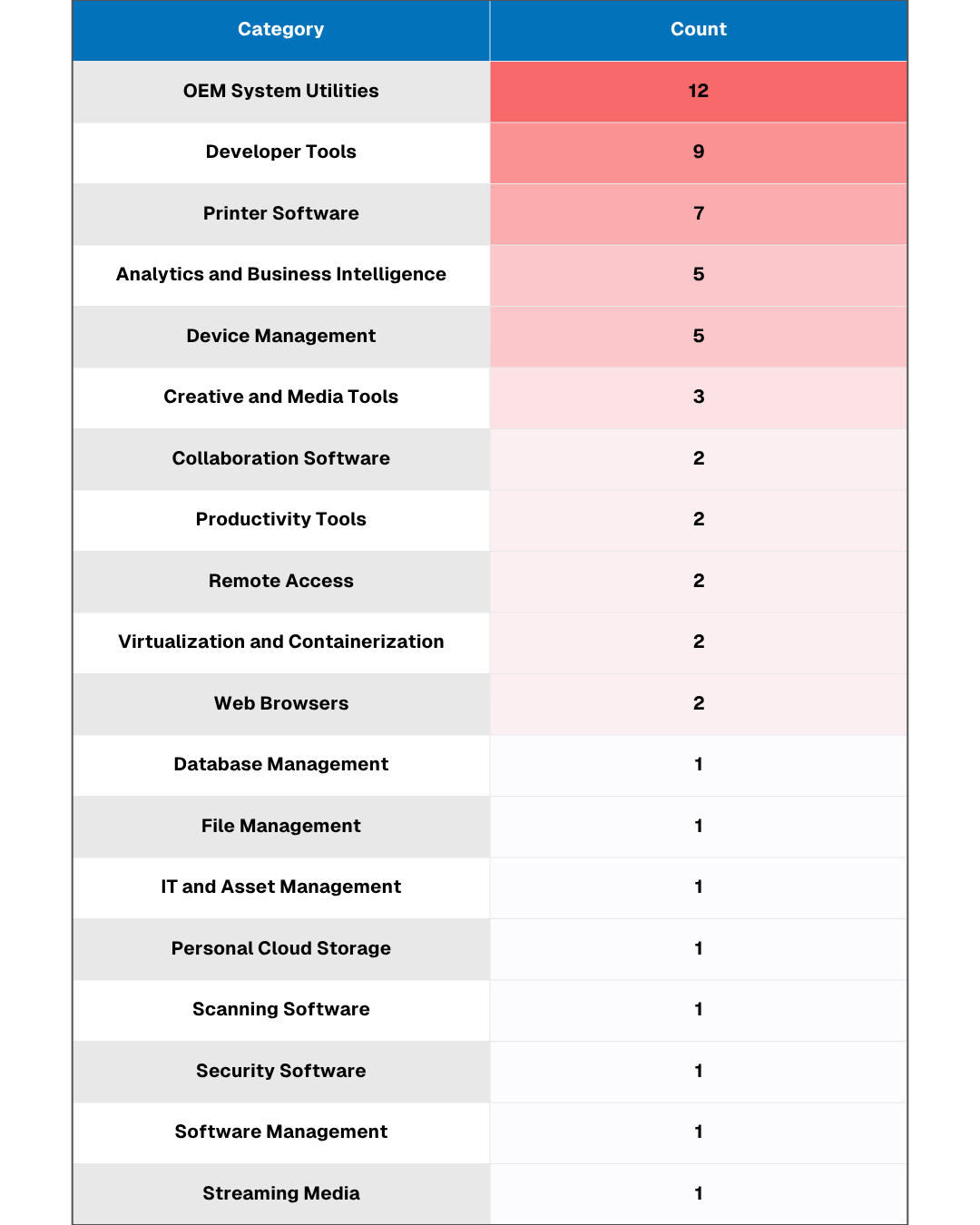
Figure 2: Count by Category (Spektion Data)
As you can see from the data Spektion identified across one customer environment, vulnerable software categories (from A to Z) include:
- Analytics and Business Intelligence
- Collaboration Software
- Creative and Media Tools
- Database Management
- Developer Tools
- Device Management
- File Management
- IT and Asset Management
- OEM System Utilities
- Personal Cloud Storage
- Printer Software
- Productivity Tools
- Remote Access
- Scanning Software
- Security Software
- Software Management
- Streaming Media
- Virtualization and Containerization
- Web Browsers
Across all analyzed software, Spektion identified an average of 7 runtime risks per product associated with unquoted path vulnerabilities.
Other compelling insights include:
One application exhibiting the flaw has a total of 19 identified runtime risks.
36 of 59 having 5 or more runtime risks (61%).
42 of 59 have 0 CVEs present (71%).
40 of 59 have “elevated risks” (average of 4.7 elevated risks) (68%).
Detection Scenarios7
In these example rules, we are using our baseline of vulnerable folder paths provided by our Spektion telemetry and searching for the execution of filenames from those known vulnerable folder names.
An example detection scenario would be monitoring for process execution in c:\programdata\vulnerable and being alerted to the execution of malware.exe from within that directory path. As you get a better understanding of your environment and the alerting from the rule, we highly recommend the addition of a known good hash list in addition to known good filenames (as filenames are easy to impersonate/spoof).
Sigma [process creation in vulnerable folder path]
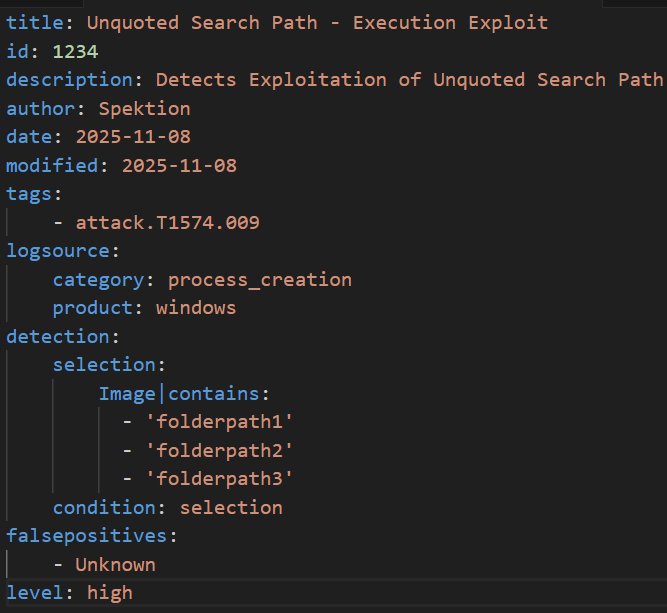
Figure 3: Sigma Example Rule
KQL [Defender]
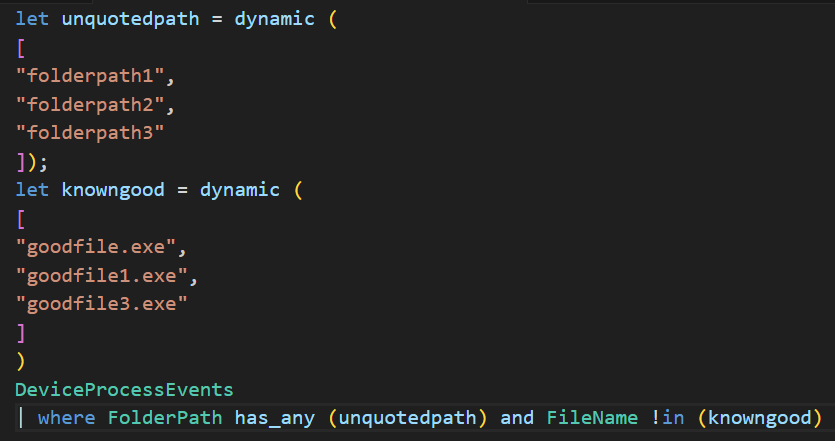
Figure 4: Example Defender KQL
Spektion8
Because Spektion observes software behavior in execution rather than relying on disclosed vulnerabilities, it identifies legacy flaws like unquoted paths even when vendors haven’t disclosed or patched them. This enables organizations to identify this and other undisclosed flaws across everything running in their environment, including internally developed tools that would never have disclosed vulnerabilities.
The images below outline a few of the data points available to the analyst within the Spektion environment for this specific runtime risk:
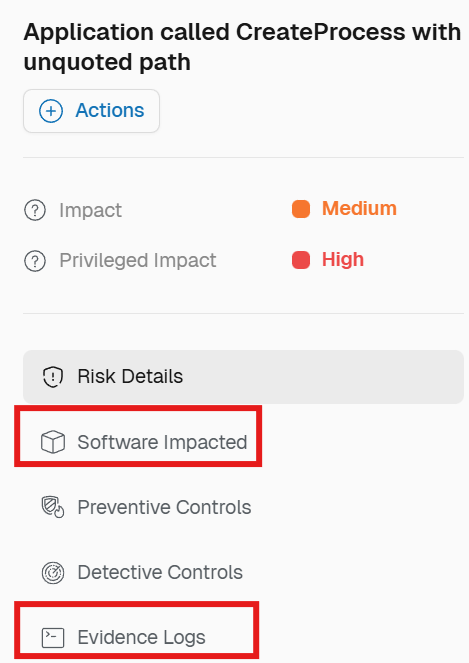
Figure 5: Navigate to the software impacted by this risk and evidence logs
The evidence logs section provides all relevant information needed to create a known baseline path list for the example detection rules outlined above.
While Spektion doesn’t depend solely on CVEs to quantify the risk of a given application, we still use it as a data point to assist in mitigation prioritization.
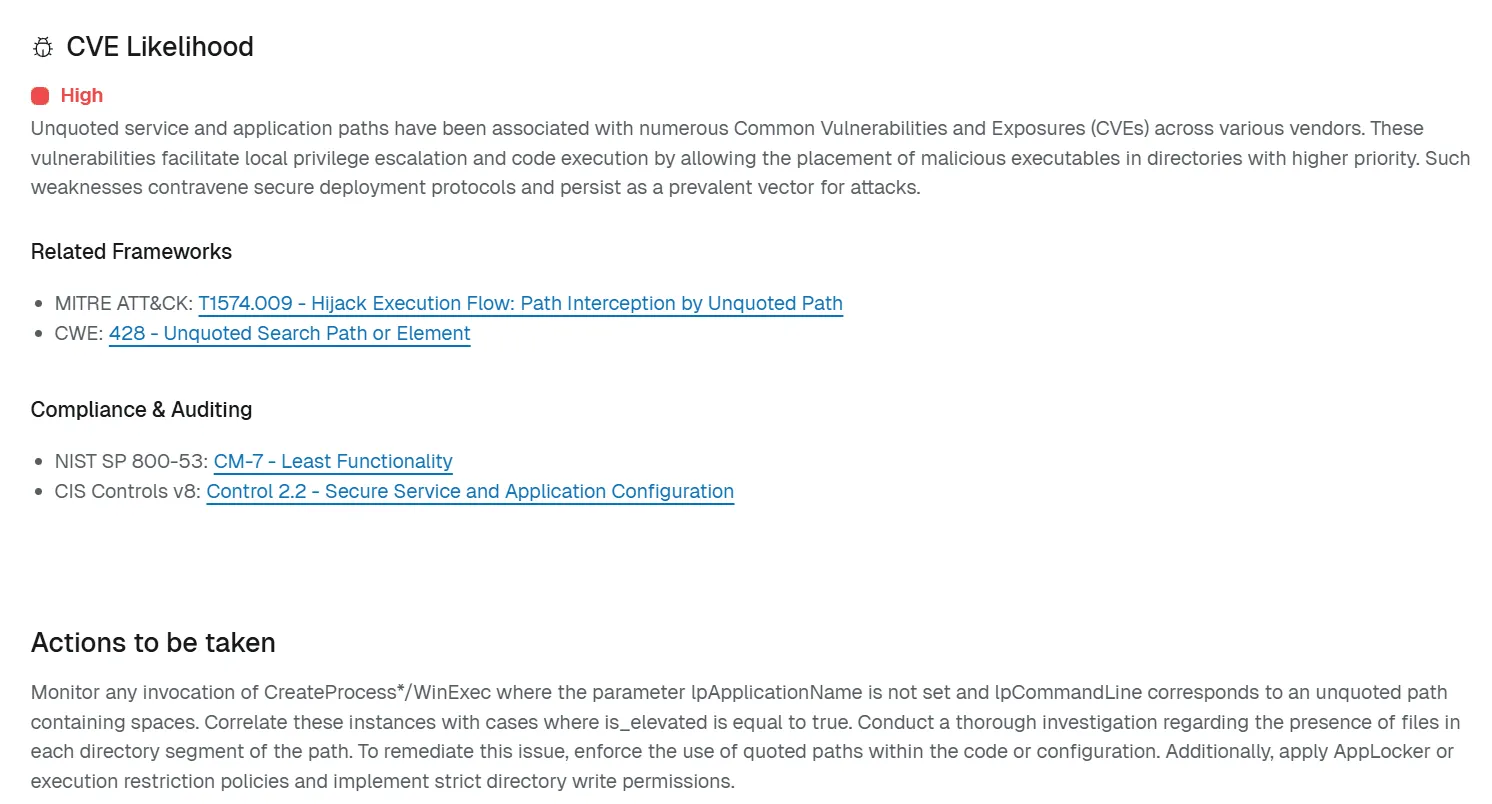
Figure 6: CVE Likelihood Detail Page in Spektion
Conclusion
Unquoted process execution paths are a legacy flaw that continues to surface in modern software, not because the risk is unknown, but because it’s invisible in the ways most organizations measure and manage software risk. Spektion’s unique visibility shows that applications exhibiting this runtime behavior almost always harbor additional insecurities, averaging six other runtime risks per affected program.
Traditional vulnerability management platforms still depend on CVEs as their starting point, but that model fails when the vulnerability is old, undocumented, or undisclosed.
Only 30 CVEs this year reference CWE-428, yet our runtime analytics have detected this flaw in 59 active applications across 19 software categories, many of which are business-critical and externally exposed.
Legacy flaws like these connect modern intrusions to 20-year-old coding errors. Runtime visibility is the only way to surface and prioritize them before attackers do. Spektion provides that visibility by continuously observing software behavior, identifying exploitable conditions like unquoted paths long before they appear in a disclosure feed.
References
3 CWE - CWE-428: Unquoted Search Path or Element (4.18)
4 CreateProcessA function (processthreadsapi.h) - Win32 apps | Microsoft Learn
5 CVEDetails.com Security Vulnerabilities, CVEs related to CWE-428
6 LOLMIL: Living Off the Land Models and Inference Libraries