How Financial Institutions Can Use Runtime Monitoring To Meet Third-Party Guidance from the Federal Reserve, NYDFS, DORA, and NCUA
Learn how runtime monitoring helps banks and credit unions meet evolving third-party risk requirements from the Fed, NYDFS, DORA, and NCUA.
Published on
Managing third-party software risk has become a significant challenge for many financial institutions. Compliance teams are expected to monitor hundreds of vendors, map dependencies, and prove continuous oversight, often with limited staff and static data.
Recent guidance from the Federal Reserve, NYDFS, DORA, and the NCUA all emphasize the same expectation: evidence-based, ongoing monitoring of third-party risk. The problem is that most programs still rely on snapshots in time that quickly become outdated, such as questionnaires, SBOMs, and static vulnerability scans.
An increasing number of institutions are filling that gap with runtime vulnerability management, which continuously observes how software behaves in your environment. Instead of waiting for quarterly updates or vendor attestations, runtime monitoring gives compliance teams visibility into risk as it emerges in real time.
In this article, we’ll show you how Spektion empowers teams with real-time discovery and continuous risk scoring across all installed applications, including third-party, internal, legacy, and AI-generated software. The result is a single, trusted source of truth that simplifies compliance and delivers a real-time view of runtime risk.
Why Third-Party Software Risk Needs Runtime Vulnerability Management (RVM)
Managing third-party software risk is inherently complex. It involves juggling vendor discovery, risk assessments, due diligence, contract management, and more. But why should you rely on outdated data and manual prioritization to navigate this complexity? Even the most mature vendor-risk programs depend on data that was true once but may no longer be true today.
Unfortunately, that’s the reality for most compliance teams today. The tools you depend on (asset registers, SBOMs, questionnaires, and point-in-time scans) often provide lagging, incomplete, and frequently inaccurate information based mostly on attestation rather than evidence:
- Asset registers of your third-party software footprint rely on manual updates, so shadow IT, plugins, and temporary installs never make the list, and version information can become stale with silent and auto-updates.
- SBOMs are point-in-time snapshots and don’t track all patches, hotfixes, or added features between major releases.
- Questionnaires are time-consuming to analyze, may not always be accurate, and can lag behind current vulnerabilities.
- Point-in-time scans using CVE-based vulnerability scanners often reveal theoretical vulnerabilities, not vulnerabilities that are actually exploitable in your specific environment.
For small teams managing hundreds of vendors, these outdated inputs create an unsustainable workload with limited measurable risk reduction.
Prioritization and scoring become guesswork, compliance is harder to prove, and with new regulations like DORA coming into effect, the burden on financial institutions (especially those with EU customers) is increasing.
Get a Real-Time Evidence Chain of Software Risk
The future of third-party risk management goes beyond questionnaires, reports, and point-in-time scans. It involves continuous, evidence-based monitoring, powered by Runtime Vulnerability Management (RVM) from a solution like Spektion.
At the heart of RVM is runtime monitoring, which observes how software behaves while it’s running in your environment so you can understand your related risk in real-time. By tracking real interactions among software, hardware, and users, you gain visibility into the exploitation paths that attackers might use, including risks that may not yet (or may never) have a CVE.
For example, RVM can detect when an application silently creates an opportunity for undetectable lateral movement by an attacker. This is something static vulnerability scans and vendor questionnaires would typically miss.
This is crucial because software with few or no published CVEs can still pose significant risks. By understanding real runtime behavior, compliance and security teams can prioritize actual vulnerabilities instead of chasing theoretical ones.
Learn more about what runtime vulnerability management is and how it works
With Spektion’s RVM, third-party risk management evolves from a mainly paperwork-based approach into an automated, data-driven process. Rather than relying on outdated inputs like SBOMs or static scans, RVM continuously evaluates the live exploitability of third-party, internal, legacy, and AI-generated software.
Through Spektion’s unified dashboard, compliance teams gain full visibility into:
- All installed software (including OEM, shadow IT, homegrown, and AI-generated)
- Runtime risk scores for each application, enriched with CVEs where available
- Software categories, versions, usage patterns, and interconnections
- Timestamped, vendor- and asset-linked evidence ready for audits
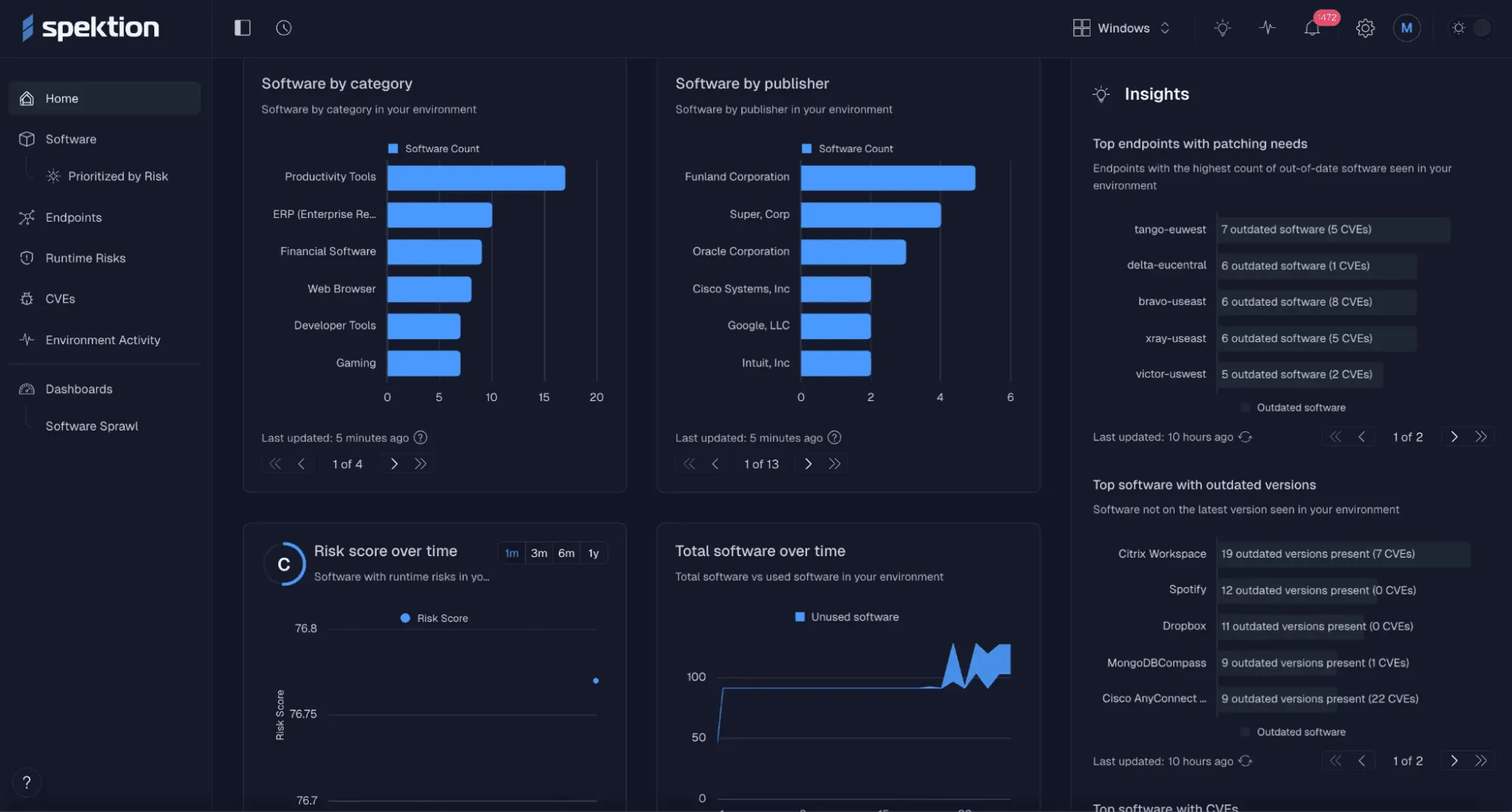
See all your installed software and associated risks in Spektion
All this data can be proven and reported automatically in a continuous record, simplifying compliance reporting and auditing processes.
Managing Financial Industry Regulations With RVM
Do you have a small team, numerous vendors, and countless potential risks? With RVM, these challenges are easily manageable. RVM allows you to instantly identify your risks and automate compliance reporting, helping you stay ahead of regulatory demands.
Below, we demonstrate how RVM empowers financial industry compliance teams to effectively navigate today’s most common regulatory challenges, quickly, accurately, and at scale.
Digital Operational Resilience Act (DORA)
Under DORA, the EU requires covered financial entities to maintain proportionate, continuous oversight of their ICT third-party providers, backed by provable evidence.
RVM automates oversight with real-time discovery (including OEMs) and runtime risk scoring to tier providers (Art. 28).
It also helps to observe dependencies, surface concentration, and third-party risk (Art. 29), and prove that controls are verified in practice to support contract clauses, change-of-risk triggers, and exit planning (Art. 30 - Art. 31).
Learn more about how Spektion aids DORA compliance
SR 23-4 Interagency Guidance (OCC/FDIC/FRB)
Interagency guidance from the OCC, FDIC, and Federal Reserve calls for a risk-based lifecycle control plan. Institutions are expected to vet, contract, monitor, and exit vendor relationships with a level of oversight that scales to each provider’s criticality.
Specifically, the guidance requires banks to perform ongoing monitoring that is “appropriate for the risks associated with each third-party relationship.” This means your oversight needs to keep pace with change.
Spektion makes this simple by observing software at runtime (without code changes or modifications to your environment), enabling real-time coverage across the entire vendor lifecycle, including procurement, onboarding, operation, and offboarding.
And because every event is timestamped and linked to vendors and assets, you’re always audit-ready.
National Credit Union Administration (NCUA) Guidance
The latest NCUA guidance expects credit unions to conduct due diligence on critical third-party providers.
RVM automates and exceeds this requirement by continuously monitoring third-party software risks in real time. With Spektion, you get runtime evidence proving that third-party software behaves as expected, eliminating the need for manual testing cycles.
New York Department of Financial Services (NYDFS) Part 500.11
NYDFS Part 500.11 expects risk-based discovery, assessment, due diligence, policies, contractual controls, and ongoing oversight of third-party providers.
RVM fully meets and often exceeds these requirements. With Spektion’s RVM, you can:
- Automatically discover all third-party software in your environment.
- Validate vendor-claimed controls to ensure they are present and effective.
- Detect runtime behavior that contradicts contracts, such as unexpected privilege escalation or unencrypted data flows.
RVM vs the Status Quo
The table below highlights how Spektion Runtime Vulnerability Management (RVM) streamlines compliance, automates key tasks, and delivers a clear advantage across every stage of your third-party software lifecycle.
| Process | Runtime Vulnerability Management with Spektion |
|---|---|
| Discover | Automatically detects all software, including vendor-provided and shadow IT assets, in real time at first run. |
| Classify | Maps each asset to vendor, product, version, category, usage, privileges, and data touchpoints for complete context. |
| Assess risk | Evaluates exploitability in your live environment using a runtime risk score, enriched with CVE data when available. |
| Prioritize | Ranks risks based on behavior, business context, and potential blast radius, generating prioritized queues with suggested controls. |
| Apply controls | Recommends actionable next steps when patching isn’t possible, including pausing, removing, or restricting software access. |
| Validate | Confirms controls are effective with runtime verification and provides audit-ready, timestamped, vendor- and asset-linked logs, plus attestations and certifications. |
| Report | Meets reporting requirements with comprehensive, timestamped logs directly from your environment. |
| Offboard | Makes it easy to locate and remove all installations cleanly, verify removal with runtime evidence, and retain exit artifacts for audits and reviews. |
Try Spektion to Enhance Compliance While Reducing Risk
Spektion helps financial institutions automate and future-proof their compliance workflows against evolving regulations and industry pressures.
Our solution works passively in your environment from a single, lightweight sensor, performing real-time, behavior-based monitoring of installed third-party software and maintaining timestamped evidence tied to vendor and asset.
Join financial services teams who leverage Spektion to scale their third-party risk capabilities while shrinking their organization’s exposure to vulnerabilities and exploitable risks.
See how Runtime Vulnerability Management transforms compliance. Schedule a Spektion demo today.