Breaking Through Data Silos: Real-Time Risk Clarity with Spektion’s Latest Release
New features enable faster workflows for security teams, audit-ready reports for leadership, and enhanced visibility to explore and act on risk.
Published on
Most security teams know the struggle: traditional vulnerability tools tell you what was possibly risky days or weeks ago, but don’t show you what’s exploitable right now.
Teams spend countless hours wrestling with fragmented reports across vulnerability scanners and endpoint inventories, manually stitching data together while critical risks slip through the cracks, and burnout from repetitive analysis tasks rises; yet, attackers keep moving faster.
Spektion’s latest release changes this dynamic entirely. With three powerful new capabilities—Report Generator, Network Insights, and an enhanced Dashboard—we bring together vulnerability data, runtime behavior, and network visibility into one platform.
The result is clear: faster analysis, actionable insights, and even more proactive ways to mitigate risk.
Report Generator: All Your Critical Data, One Click Away
Traditional security tools trap your data in separate silos. Want to identify which endpoints are running unused software with critical CVEs? Get ready for multiple exports, hours of manual correlation, and lots of spreadsheet wrangling. If you need to combine vulnerability findings with runtime behaviors, such as insecure certificate management and network activity, the analysis becomes even more complex, spread across even more disconnected systems.
That’s where Spektion’s Report Generator comes in. Instead of hours lost stitching spreadsheets together, you get one tool that expands the breadth and depth of your vulnerability risk analysis:
- Correlate data across silos: Easily correlate data across software inventories, endpoint configurations, CVE databases, and behavioral risks, all in one place. Want to identify all instances of a specific software version across endpoints, view its published CVEs, and overlay runtime behaviors such as excessive account access? Done.
- See runtime risks before they become CVEs: Our runtime vulnerability detection continuously monitors software execution patterns, identifying privilege escalation, memory mismanagement, file operations in public locations, and other insecure behaviors. This real-time analysis identifies exploitable conditions like DLL hijacking vulnerabilities, insecure certificate handling, privilege abuse, and other risky behaviors that often appear before they’re cataloged in CVE databases.
- Supercharge threat hunting: Build custom reports that tie together runtime risks, endpoint data, and vulnerability details in one place. Instead of manually stitching context together, analysts can pivot across software, CVEs, and runtime behaviors instantly, accelerating investigations and hypothesis-driven hunts.
- Focus on the use cases that matter to you: Identify unused software per endpoint, generate complete CVE + runtime risk assessments to cover all of your software, and create prioritized remediation plans based on the software most likely to be exploited.
One Spektion customer cut vulnerability triage from hours of spreadsheet analysis to 15 minutes using Report Generator.
See how Report Generator simplifies vuln management → Book a demo
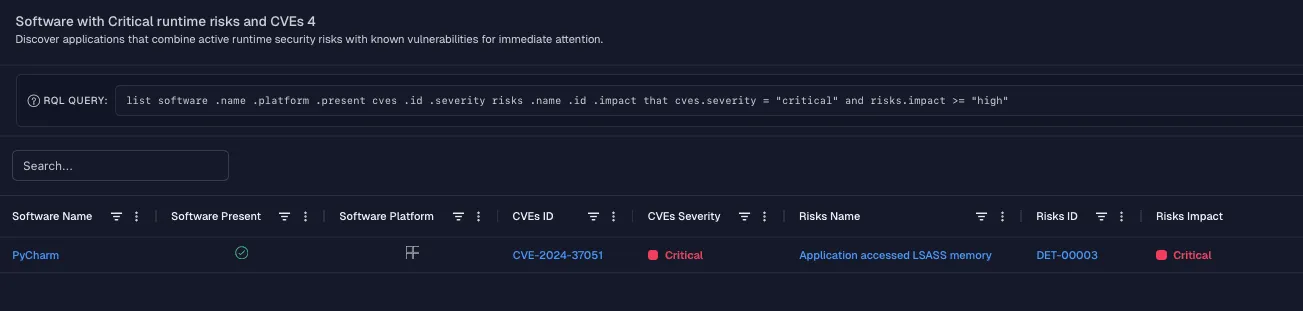
Create advanced reports, such as “all software with both critical risks & CVEs.” Click into a row to view affected endpoints, allowing you to act quickly.
Network Insights: Visibility Where It Matters Most
Vulnerability scans can show you what’s installed, but they don’t reveal how software behaves on your network. That blind spot has led to countless breaches.
Network Insights fills the gap, adding a new dimension to how you understand vulnerability risk:
- Uncover software network activity: See comprehensive software network telemetry on a per-endpoint or per-software basis, identifying which applications are making outbound connections and which are listening for inbound traffic—critical data for assessing exploitation risk.
- Map inbound listening activity: Tie network sockets to specific application processes, identifying which software is accepting connections on which ports. Combined with vulnerability data, this process-level attribution highlights the riskiest targets—software that is both exploitable and network-accessible. Unlike port scanning approaches, this method provides continuous, real-time visibility into listening services as applications start, stop, and modify their network behavior.
- Spot anomalous activity: Identify new or unusual network connections introduced in software updates. Correlating these changes with runtime risks or vulnerabilities helps uncover software that may be introducing malicious behavior.
The riskiest software isn’t just installed; it’s what’s quietly listening on your network.
Discover hidden risk in your network → Request a walkthrough
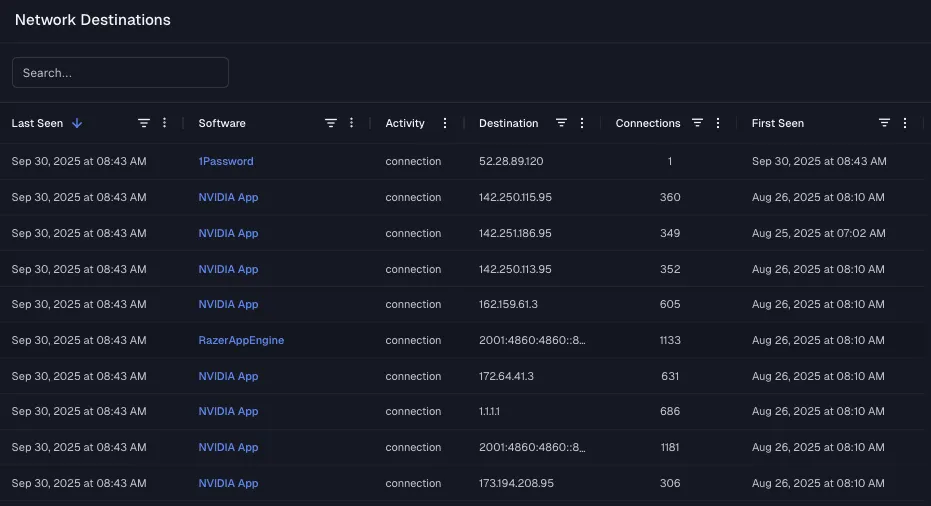
Don’t guess where your software is connecting. Spektion shows you every network destination, so you can quickly spot anomalies and reduce attack surface.
Enhanced Dashboard: Your Security Command Center
We redesigned the home dashboard to transform how teams act on data. After logging in, users are directed to a single page that consolidates estate-wide attack surface trends and critical risk metrics. Interactive charts make it easy to click and drill down from high-level overviews directly into specific vulnerabilities. The whole experience is faster, clearer, and built to drive action.
- Click-to-drill exploration: Investigate issues directly from charts and widgets with a single click.
- Track software sprawl: Monitor installs, unused software trends, and publishers with the largest exposure footprint.
- Single source of truth: The dashboard provides real-time inventory that combines security risk details with category, publisher, and utilization data. Security and IT teams no longer need to reconcile multiple systems, as everything, from vulnerability exposure to software usage, is visible in one view.
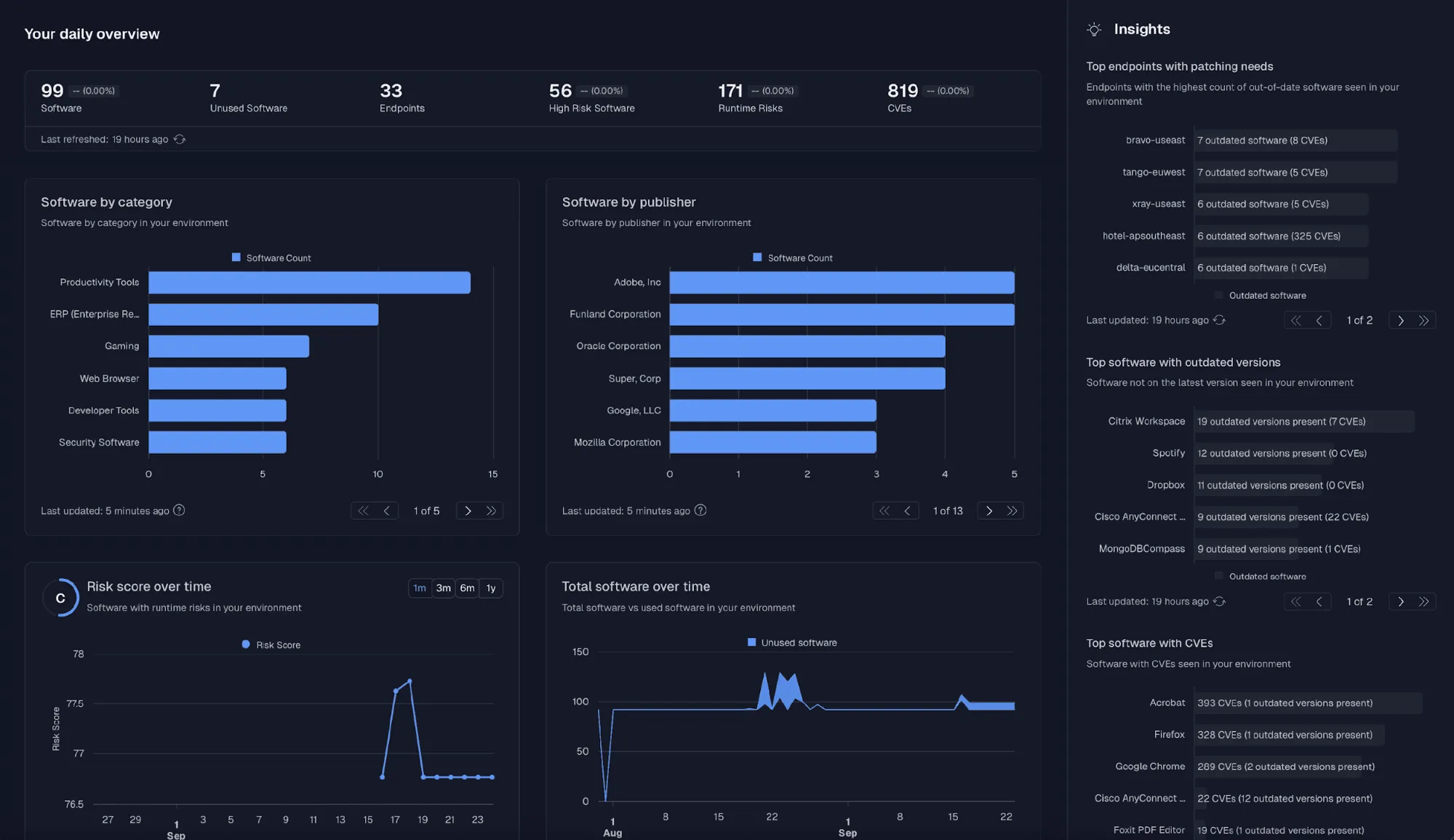
Understand your estate at a glance with Spektion's redesigned dashboard experience.
Why This Matters
Today’s enterprises aren’t just dealing with “more vulnerabilities.” They’re facing a perfect storm of scale, complexity, and speed. The attack surface continues to expand, while the resources available to manage it remain the same. That tension shows up in three persistent challenges:
- Software sprawl: The increasing velocity of new tools and versions, exacerbated by AI-enabled software development, makes it nearly impossible to maintain an accurate inventory of software risk across endpoints and systems.
- Unpatchable or unprioritized vulnerabilities: Security teams can’t patch everything, and CVSS scores alone don’t provide enough coverage or context to decide what matters most.
- Attacker speed: Adversaries, increasingly leveraging AI tools, are identifying and exploiting software faster than defenders can react, often before CVEs are even disclosed.
Spektion addresses these realities head-on, giving security teams the clarity and control they need to move faster against risk:
- Comprehensive visibility: A unified, contextualized inventory of all software—used, unused, vulnerable, or risky—so teams can finally manage sprawl with confidence.
- Beyond patching: Runtime risk detection surfaces exploitable conditions before CVEs exist and provides custom mitigations to reduce risk even when patching isn’t an option.
- Preemptive threat management: By correlating runtime behavior, vulnerabilities, and network data, Spektion operationalizes vulnerability reporting for threat hunting teams searching for exploitation.
The Bottom Line
These aren’t incremental features; they’re a new way to manage vulnerability and software risk:
- From siloed data → unified correlation
- From reactive CVEs → proactive runtime risk
- From producing patching tickets → contextualized, real-time inventories and preemptive mitigations
- From static reports → dynamic network visibility
The threat landscape isn’t slowing down. Now your security operations don’t have to either.
Ready to move beyond CVEs? Talk to our team and see how these new capabilities transform your vulnerability risk management.