There’s An Easier Way to Meet DORA ICT Third-Party Risk Requirements
Learn how continuous runtime monitoring simplifies DORA Chapter V compliance for banks, insurers, and other FSIs.

Published on
Embedding third-party risk management into an ICT risk framework (as required by DORA Chapter 5 “Managing ICT Third-Party Risk”) is no small task. In one survey, 34% of EMEA financial services respondents named it the single most challenging DORA requirement, making it the top compliance hurdle overall.
The good news is that solutions now exist to make this process far more manageable.
Third-party risk management solutions, such as Spektion, help DORA-covered entities replace or augment periodic, labor-intensive risk monitoring with a real-time view of third-party risk from all their installed software.
In this article, we’ll show you the DORA third-party risk management options that firms like banks, insurance companies, payment providers, and other FSI companies have. Plus, why more financial institutions are using runtime visibility technology to assess and manage their third-party risks.
DORA-Governed Organizations Have Two Options for Third-Party Risk Management
The Digital Operational Resilience Act (DORA) came into effect on January 17, 2025, and applies to entities providing financial services in the European Union.
Since then, all covered entities (as defined in Article 2 and certain ICT third-party providers) must comply, to some extent, with the ICT third-party risk management requirements outlined in Chapter V (Articles 28–44).
DORA Chapter V outlines the procedures for assessing contracts, tracking ICT asset concentration, evaluating risks in new deployments, and reporting to regulators, among other obligations.
Currently, there are two potential paths to meet this requirement for understanding third-party risk.
Option 1 - Static DORA compliance
One way to approach third-party risk management is to treat it as a series of fixed checkpoints: SBOMs at onboarding and major releases, scheduled questionnaires, and occasional scans.
While this approach can satisfy requirements on paper, it has two major drawbacks:
a) gaps between “checkpoints” (e.g., when new software versions are released), and
b) high costs and labor demands, making it difficult to scale.
Option 2 - Continuous DORA compliance and third-party risk monitoring
Another, more efficient approach to third-party risk management is to adopt continuous monitoring of all installed software, giving DORA-governed FSI teams a live, always-current view of third-party software risk.
This approach utilizes runtime detection software, such as Spektion, to identify new versions and swapped components upon their release, so SBOM visibility stays accurate and no gaps form between review cycles.
Because the risk inventory and behavior context update in real time, there’s no need to rerun periodic, labor-intensive assessments to stay current.
Another significant DORA compliance advantage from a continuous approach is the evidence collected. As events happen, runtime evidence is automatically tied to vendors, assets, and timestamps, which makes period-wide proof simple to produce.
Findings flow into prioritized queues with clear next actions/configuration changes, compensating controls, or detections routed to SIEM/EDR. This shifts DORA from a static, snapshot-driven exercise into a real-time practice where visibility, mitigations, and reporting are always on.
The result: a far less labor-intensive and much more cost-effective way to manage third-party risk.
Live Software Visibility Is The Simple, Safe, and Scalable Solution For DORA Third-Party Risk Management
With the insights Spektion provides, financial entities can:
- Tier risk proportionately (DORA Art. 28).
- Identify concentration and subcontracting exposure (Art. 29).
- Write, test, and police audits, SLA, location, incident, and exit clauses your contracts must contain (Art. 30).
Spektion’s Runtime Vulnerability Management (RVM) delivers runtime risk visibility that goes beyond CVEs—surfacing threats as they emerge in software behavior, not just after disclosure. It builds behavior baselines for software across your estate, including third-party and OEM tools that often fall outside traditional CMDBs or scanner coverage, or are only checked periodically.
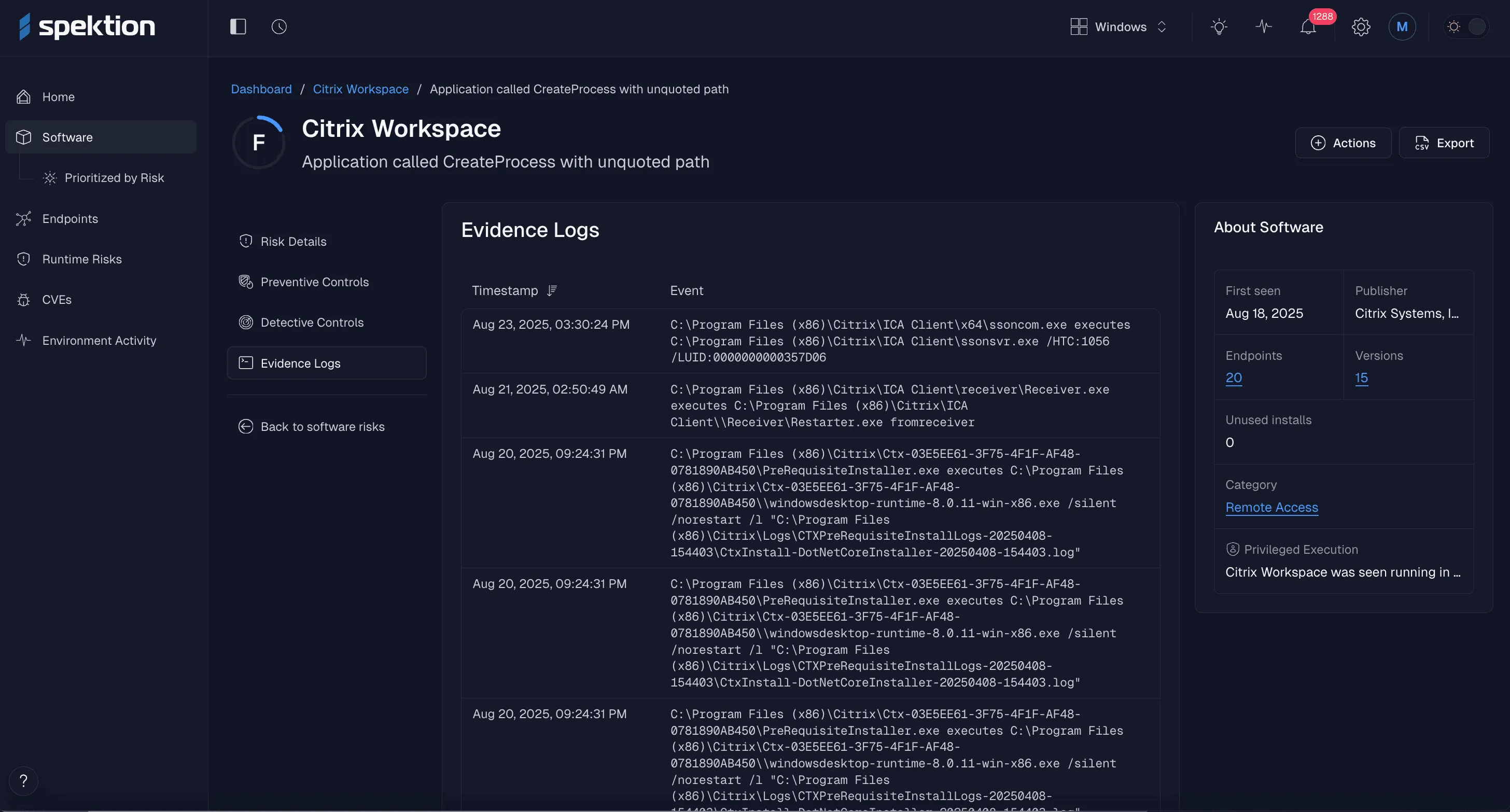
With Spektion, a DORA-covered entity can immediately discover all its installed software and:
- Produce and review live evidence trails that show what third-party software does before entering into a contract with a vendor.
- Create up-to-date asset/software inventories by finding shadow IT, unused tools, and unmanaged applications.
- Identify dependencies and plan transitions using real usage and risk data, rather than estimates, to minimize disruptions.
- Generate rich reports from security incidents to satisfy regular reporting requirements.
- Demonstrate (and use) an effective risk management strategy for software that cannot be patched or replaced easily.
These capabilities directly align with the ICT third-party risk requirements outlined in DORA Chapter V. The table below maps them, along with other DORA Article 28 requirements, to Spektion’s capabilities.
| DORA Chapter V reference & requirement | What auditors expect to see | What Spektion gives you |
|---|---|---|
| 28(1) Responsibility & proportionality | Risk-tiering of third-party apps tied to control strength and review cadence | Risk understanding of all installed software based on runtime behavior + mapped control set and mitigation options |
| 28(3) Contract register & yearly reporting | Up-to-date register of all ICT contracts split by critical/important; supervisor report/export | Live software & service register from runtime discovery |
| 28(4) Pre-contract checks & due diligence | Due diligence memo before signing; risk assessment, including concentration; conflicts log | Real risk assessment of live software during POC before deployment beyond SBOM data |
| 28(5) Security standards fit | Evidence that a provider meets current security standards; cross-check of claims | Actual evidence of secure or insecure software behavior. |
| 28(6) Audit & inspection plan | Risk-based audit plan with frequency/scope; competent auditor capability | Audit planner driven by actual risk observed during deployment |
| 28(7) Termination triggers | Contractual trigger list tied to objective indicators; change logs | Change-of-risk alerts, which show adherence to the contract or drift |
| 28(8) Exit & transition | Tested exit plan; transition records; data return steps | Real dependency map based on software interactions |
DORA also mandates “appropriate” annual testing.
In most cases, Spektion’s runtime vulnerability management capabilities can significantly contribute to meeting this compliance requirement.
Where regulators demand further testing, such as a DORA-specified Threat-Led Penetration Test (TLPT), Spektion can enhance visibility and improve reporting by providing an added layer of runtime risk scoring.
See ALL Your Installed Software Risks (Including Third-Party Software)
The core advantage of runtime vulnerability management is its ability to show you risk across your environment without relying on CVEs.
While traditional vulnerability management solutions scan for applications and compare signatures to a database of known exploit risks, Spektion observes real-time application behavior to score the exploitability of software in your actual environment.
Here’s how Spektion works:
- A passive, lightweight agent observes live software behavior at runtime.
- New insecure behavior is flagged based on a proven and transparent runtime scoring system to indicate exploitability even without a CVE.
- Risks are presented and prioritized by runtime context and enriched where CVSS/Intel exists to produce a runtime risk score.
- You get actionable next steps that go beyond patching, such as configuration hardening, control-based mitigations, or detection rules for your SIEM/EDR.
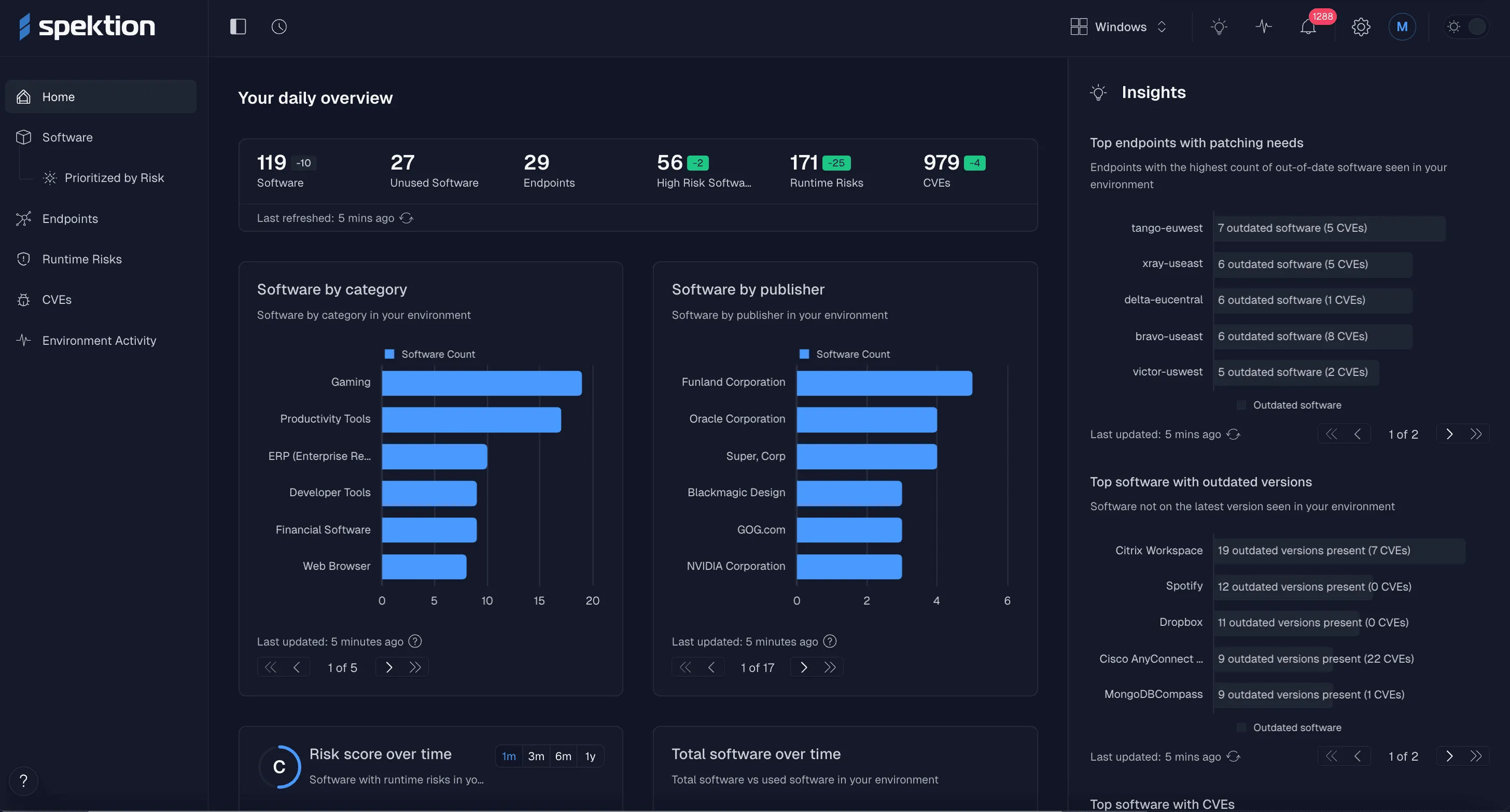
With Spektion, FSI companies can see risk at the macro level (i.e., throughout their environment, like the screenshot above) or examine the risk behavior of individual software assets with detailed logs and MITRE ATT&CK mappings.
Spektion Is A Continuous DORA Third-Party Risk Management Solution
Meeting DORA third-party risk management requirements is easier when you have visibility into the actual behaviour of third-party software running in your environment.
Spektion deploys in minutes and integrates with your existing security stack.
It gives you a real-time view of risk scores, mitigations, and reporting pathways to make DORA compliance far less stressful and costly than it otherwise would be.
Book a personalized Spektion demo, and we’ll walk you through exactly how it fits into your DORA third-party risk management workflow.