CTEM Program Visibility Gaps and How to Close Them at Runtime
Strengthen CTEM programs with runtime insights into software risk to reduce blind spots and exposure.

Published on
Continuous Threat Exposure Management (CTEM) is quickly becoming the gold standard for organizations seeking a comprehensive understanding of their software risk landscape. Yet even the most mature CTEM programs can miss a critical blind spot: what’s actually running inside your environment.
Traditional visibility approaches, such as asset inventories, vulnerability scanners, or external threat feeds, often focus on known vulnerabilities or external-facing assets. But the reality is that third-party software installed in your environment can behave dangerously even without a recorded CVE, creating exposures that remain invisible until they become incidents.
For security teams running a CTEM program, understanding and managing this “hidden half” of software exposure is critical.
Without accounting for all installed and running software, a CTEM program may underreport risk, misprioritize remediation, or leave exploitable software unchecked. Real risks in installed software can be invisible or underscored without software runtime visibility.
The CTEM framework confronts a vulnerability management reality: you cannot fix everything. Some risks can, and should, be safely ignored while others demand urgent attention. To manage risk accurately enough to do this (and unlock the two-thirds reduction in breach risk Gartner ascribes to CTEM), program tooling cannot rely on CVEs, signatures, or lagging indicators of risk.
Software Vulnerabilities Are Fueling Breaches Faster Than Teams Can Respond
The 2025 Verizon DBIR makes the business case for CTEM crystal clear: software vulnerabilities are fueling breaches at a scale and speed security teams can’t keep up with, which means traditional approaches to vulnerability management are failing fast.
Key takeaways:
- Software vulnerabilities are now the #2 cause of breaches, up 34% year-over-year.
- 70% of espionage-driven breaches started with a software exploit.
- Many exploited vulnerabilities occurred before disclosure or patch availability, leaving defenders in the dark.
Internal, legacy, and shadow-installed software can account for 20-40% of an organization’s software footprint, yet these assets are often invisible to traditional scanners or CTEM-aligned solutions.
Without runtime visibility into software installed in your environment, security teams can be missing the “hidden half” of exposure that drives real-world breaches.
Why Runtime Visibility Is Essential for CTEM Programs
Solutions that provide continuous runtime visibility and behavioral insights into third-party software installed in your environment fill this gap. They enable teams to identify which applications are actually exhibiting risky behaviors and prioritize mitigation based on actual exposure.
By including installed software in a CTEM program, organizations can significantly reduce blind spots and lower their likelihood of cyber incidents. As noted by Gartner, CTEM is also the key to making informed risk decisions across complex environments.
Concrete results from Spektion customers following the CTEM framework speak for themselves.
One customer environment revealed 215 remote access tools through runtime monitoring, highlighting previously unseen exposure. Another Spektion customer reduced their exposure footprint by 27% in 30 days by identifying and removing unused software they were previously unaware of.
With Spektion, customers have also:
- Reduced exploitable software by double digits in weeks.
- Lowered license and maintenance costs from unused software.
- Reduced incident likelihood through early mitigation of pre-CVE risks.
How CTEM Programs Use Runtime Visibility with Spektion
Runtime visibility and vulnerability management solutions like Spektion make CTEM practical and actionable, even in environments with:
- Third-party software assets
- Internally developed applications without CVEs
- Legacy solutions and shadow IT
- Incomplete software registries
Spektion is more than a “CTEM-enabling tool,” it’s a solution that integrates runtime insights directly into your CTEM workflow.
Here’s how Spektion supports the five CTEM steps.
1 - Scoping: Scope your internal software environment in real-time
Runtime visibility lets you immediately (and in real time) put installed software assets in or out of scope for your CTEM program based on an array of live filters.
With Spektion, you can immediately inventory, identify, and assess every piece of software in your environment, filter a target list of assets based on their behavior, domain, and other factors, and see a live risk score for your selection.
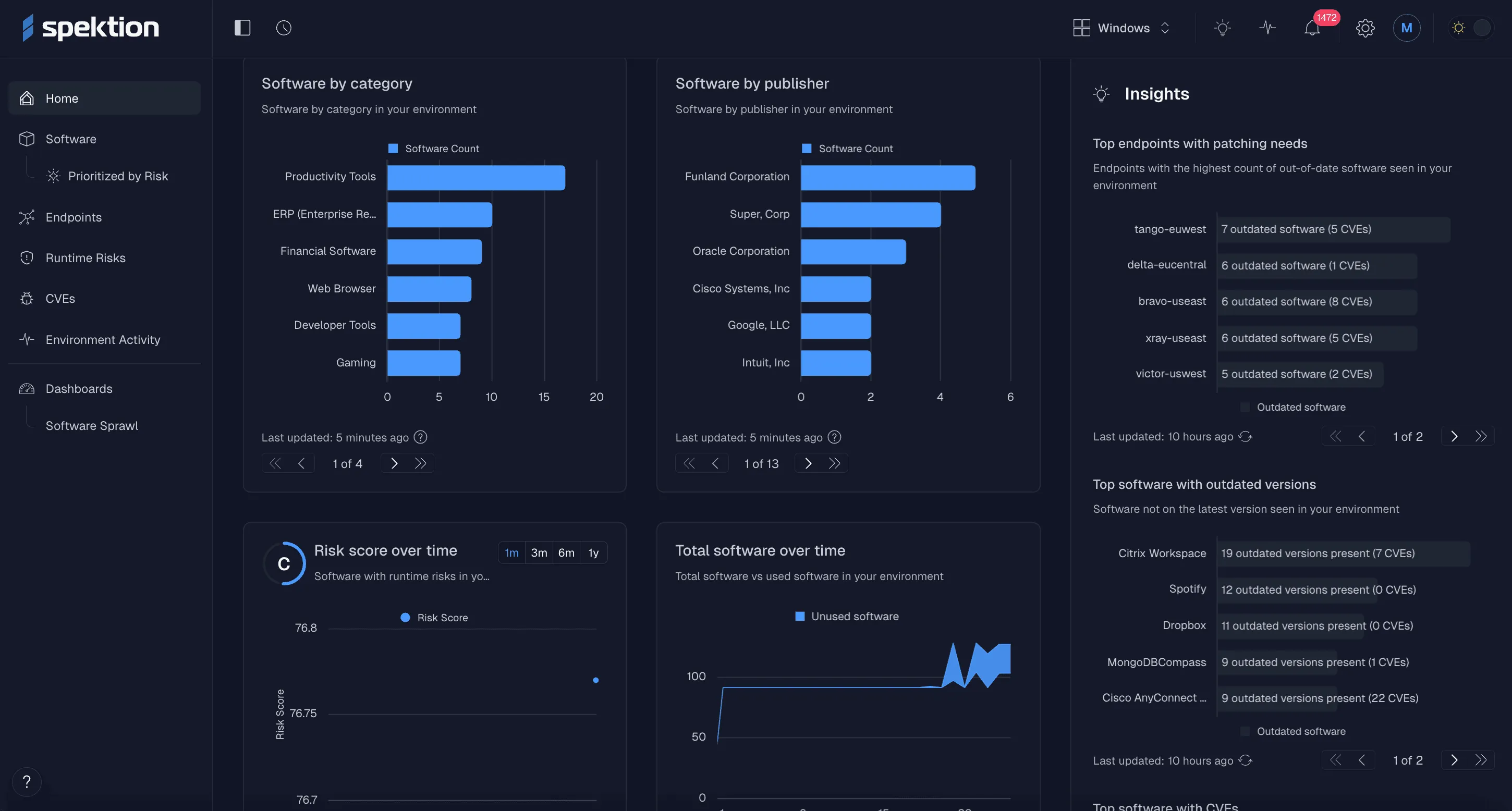
See all your installed software and its risk
For example, you could use Spektion to immediately scope software running on critical systems like domain controllers, or find and include only third-party apps or software of unknown origin.
We help you scope based on your real software inventory, not just what’s in your registry, saving time in later CTEM stages and creating a source of truth for CTEM progress.
2 - Discovery: Comprehensive IT inventory audit of all known and unknown software installs, including version numbers, usage history, and more
With runtime visibility, you can discover active software risks from runtime and get an accurate understanding of vulnerabilities in assets installed in your environment.
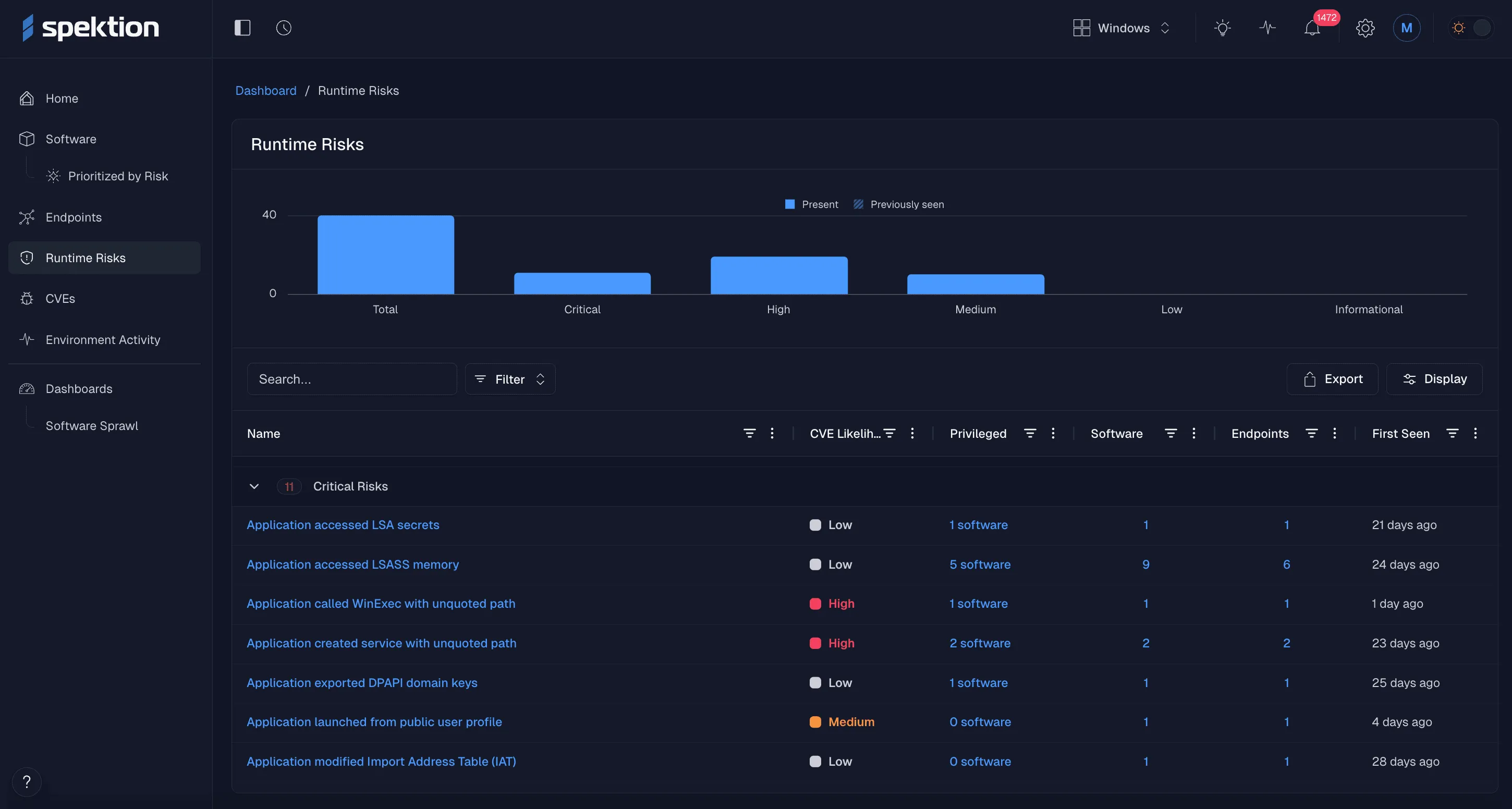
View your risk at runtime
Monitoring runtime activity provides precise insights into risk based on actual software behavior, enriched with CVE data when available. This allows CTEM programs to detect exploitable vulnerabilities when they emerge, even before any CVE exists.
You can also see the risks within your in-scope assets at a glance and get instant notifications about new installs and new risk alerts the moment new software appears or an existing app starts behaving dangerously.
For example, suppose a new version of an in-scope application starts making unusual network connections or modifying memory protection settings. In that case, you can immediately identify the behavior and apply preventive or detective controls as needed.
3- Prioritization: Use real software behavior as a live source of truth for risk
The number one success factor for any CTEM program is the ability to filter and prioritize risks accurately.
Runtime visibility is the first technology that enables teams to easily score risk based on actual installed software behavior (not just theoretical vulnerabilities) and confidently prioritize in a CTEM program.
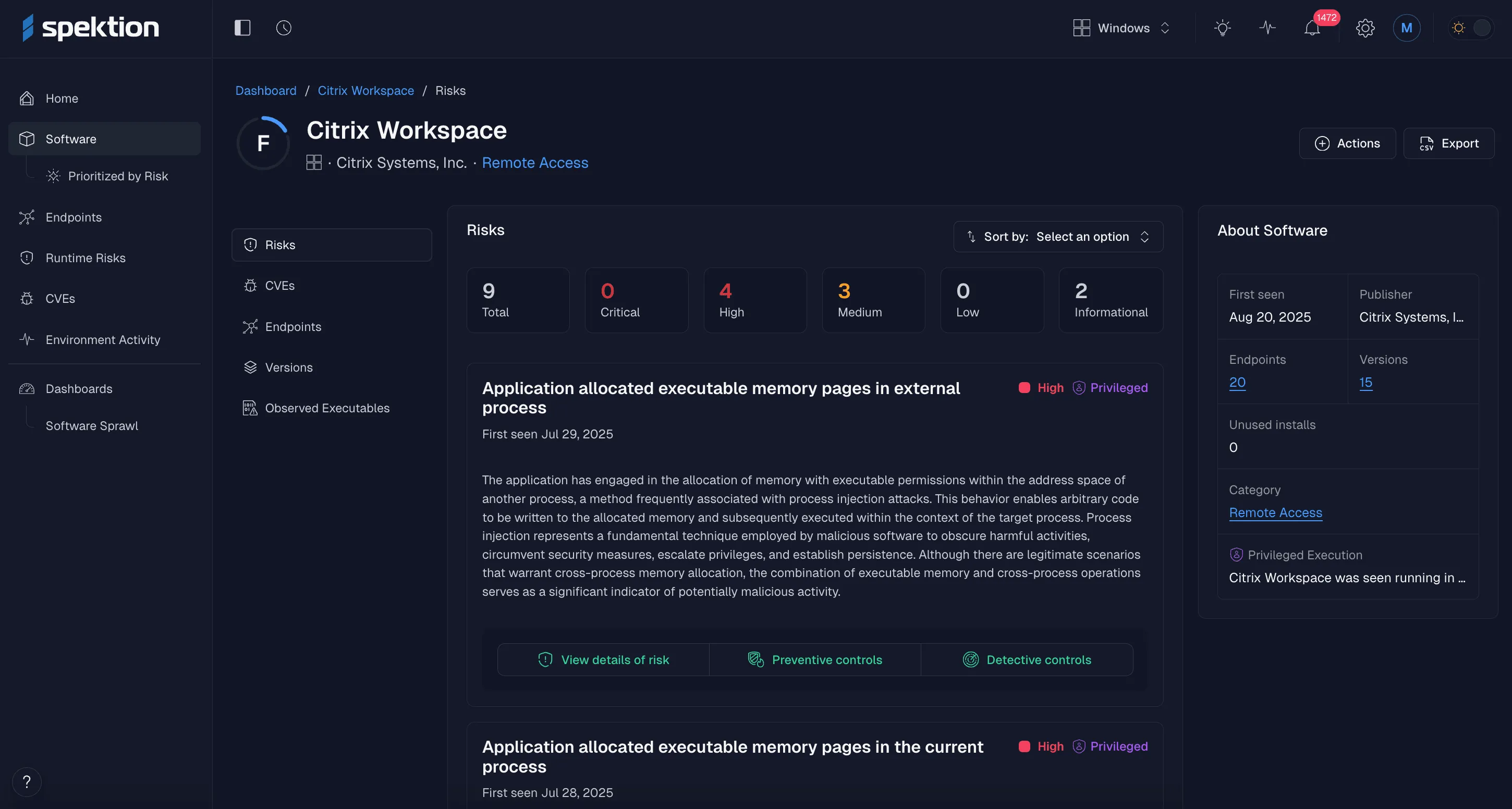
See the risk in specific software
Spektion provides clear, detailed reasoning for every runtime risk scoring. This allows you to prioritize risks with precision or quickly communicate them to non-technical stakeholders.
Runtime risk scoring reflects not only the exploitability of the asset but also its potential impact (“blast radius”) if it is exploited. With it, CTEM programs can make confident prioritization decisions that otherwise would be impossible.
4 - Validation: Map exploit risk, likelihood, and impact
Spektion’s runtime visibility enables you to perform CTEM validation based on an understanding of live software behavior.
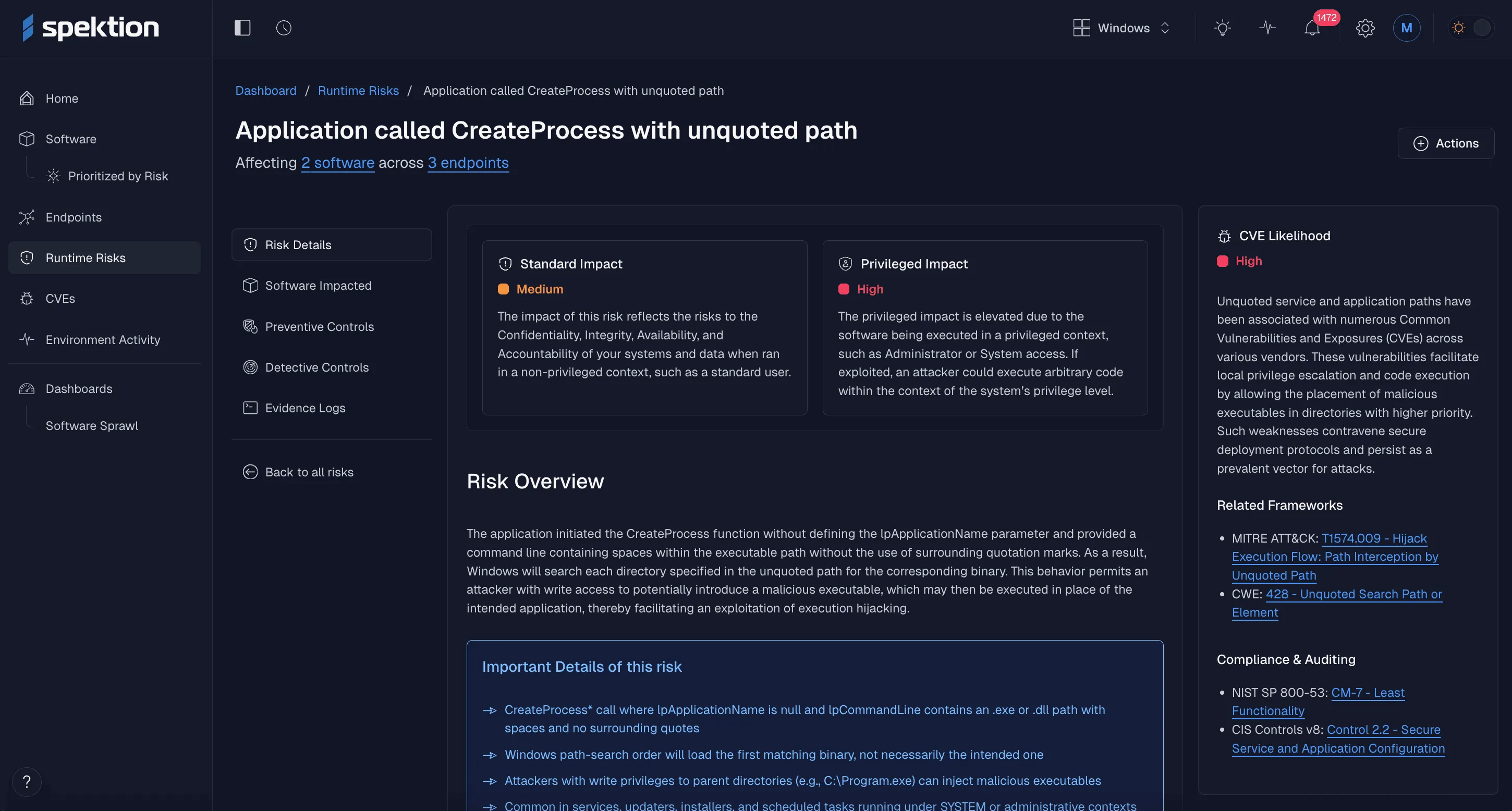
See risky software behavior right now and get the controls to mitigate threats
By combining vulnerability context, live behavior, and communication patterns, Spektion validates which software risks are genuinely exploitable, so organizations with CTEM programs can act on the most critical threats first.
We explain in plain language why risks exist, while also providing the technical details needed for deeper validation when required.
5 - Mobilize: Get customized mitigation options other than patching
Since patching isn’t always possible, runtime threat visibility provides a clear plan for risk mitigation via detection and/or prevention controls, ensuring protection even when a patch is unavailable or cannot be applied quickly.
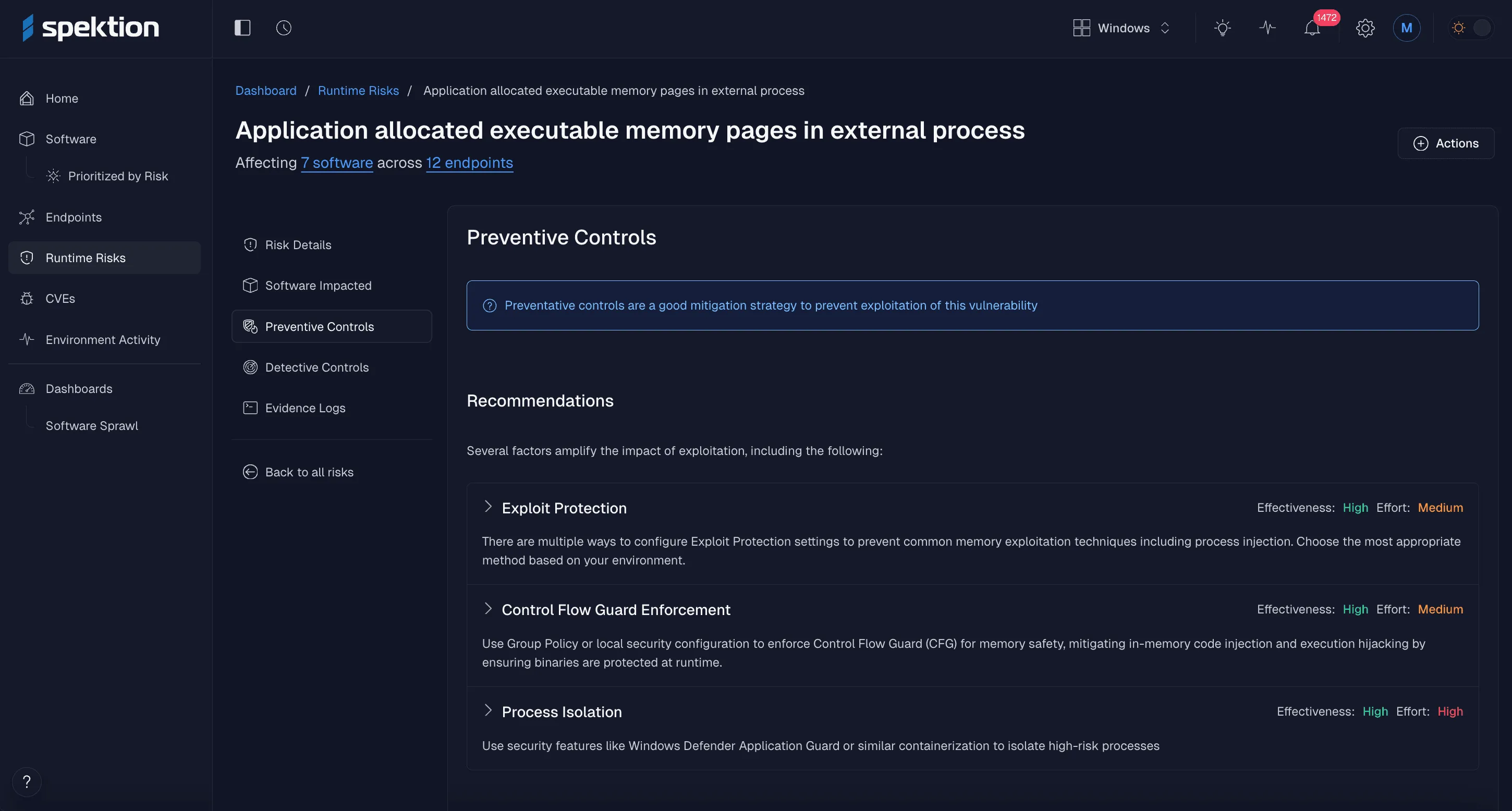
See controls to reduce exposure
For each confirmed software risk, Spektion delivers prioritized remediation recommendations. These include actionable compensating controls, such as safe removal of applications, configuration changes, or ongoing monitoring, enabling teams to respond with precision.
By tracking these actions over time, Spektion helps CTEM programs measure the reduction in exposure from software sprawl and maintain a continuously optimized software footprint.
Include Installed Software Risk in Your CTEM Program
CTEM programs cannot focus only on SaaS or IP-addressed assets. Some of the most interconnected and exploitable assets in your environment are installed software. Hundreds of internally developed tools, citizen-developed apps, virtualization apps, and file-sharing solutions are directly installed on your network, and most are missed or poorly assessed by traditional scanners.
With Spektion, CTEM teams can immediately:
- Scope from a live map of executed software and the systems it runs on, identifying software and systems executing critical/risk functions.
- Discover and maintain real-time visibility into the full list of software executing in the environment and associated vulnerabilities, including those not captured in CVEs.
- Prioritize risks using runtime exploitability, MITRE ATT&CK mapping, and blast radius of exploitation.
- Validate using live runtime evidence, to include seeing if exploitable software actually executes on all systems where it’s installed.
- Mobilize through tailored hardening guidance, uninstall/reconfigure recommendations, tailored SIEM/EDR detections, and tracked exposure reduction.
Spektion installs in minutes, integrates with existing tooling, and transforms installed software from a hidden risk into a visible, actionable component of your CTEM program.
See Spektion in action: request a free personalized demo and experience how runtime visibility bridges the gap between CTEM theory and operational reality.